The New Quiet Break-Ins: How Criminals Hack Windows Using Its Own Tools
December 2, 2025
Cybercriminals have begun adopting a stealthier and more effective way to break into Windows systems. Instead of bringing suspicious malware that security software can instantly recognize, they now turn Windows’ own legitimate components into weapons. This tactic—known as “living off the land”—allows them to infiltrate networks while blending in with everyday system activity, making their presence extremely difficult to detect.
Cybercriminals have begun using a much stealthier method to compromise Windows systems. Instead of bringing their own hacking tools—which security software can easily recognize—they now rely on legitimate Windows components already present on every machine. These include PowerShell, Windows Management Instrumentation (WMI), Certutil, Bitsadmin, scheduled tasks, and Windows services. All of them are official Microsoft utilities used every day by system administrators.
Because these programs are trusted by default, security software normally doesn’t treat their activity as suspicious. This is the core of the new technique: attackers “live off the land,” blending malicious actions into what looks like routine system work.
The difference this makes became clear during a real red-team exercise. A security tester first tried a classic method: uploading a password-dumping tool to steal credentials. The moment the file landed on the machine, the company’s security staff detected it and blocked the attack—only fifteen minutes later. Signature-based protections react instantly to known malware files, so this approach failed almost immediately.
But when the same tester switched to using only built-in Windows tools—PowerShell for reconnaissance, WMI for remote actions, scheduled tasks for persistence, Certutil for fetching files, and Bitsadmin or even email programs for quietly transferring data—the results were dramatically different. With this method, he remained undetected for three full weeks, moved laterally across 15 systems, and exfiltrated data without triggering a single alert.
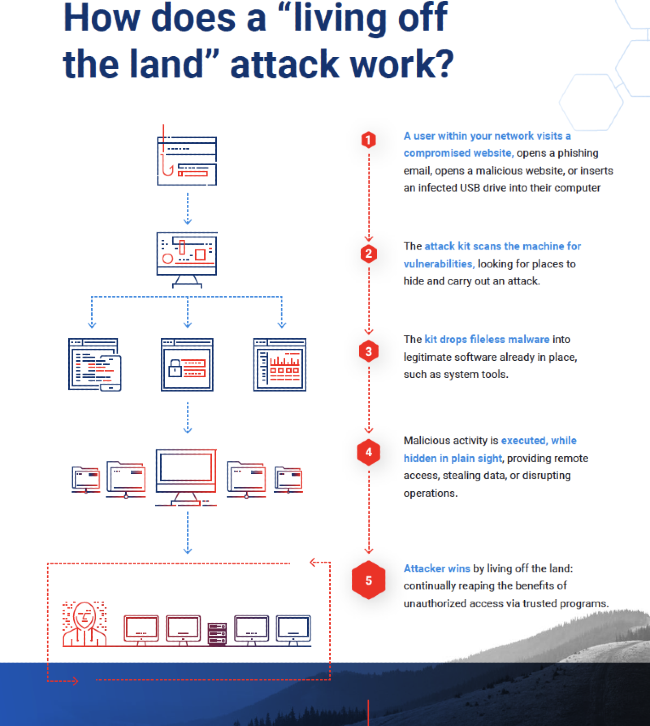
However, this technique, as powerful as it is, doesn’t guarantee indefinite invisibility. It works mainly because defenders often don’t monitor the detailed behavior of these legitimate tools. Once companies start using deeper logs, script-block monitoring, command-line auditing, and tools like Sysmon, unusual behavior stands out even when the tools themselves are trusted. Over time, organizations build baselines of what “normal” administration looks like. Any deviation—like PowerShell running odd commands, WMI creating unexpected processes, or Certutil making strange network connections—becomes detectable.
This is why the window of invisibility is limited. As defenders move beyond file-based detection and toward behavioral analysis, even Microsoft-signed utilities become part of the threat landscape. Attackers can hide for a while by blending into normal system activity, but eventually their abnormal patterns reveal them.
In short, criminals are exploiting Windows’ own trusted tools to break in quietly—but as defensive monitoring improves, the effectiveness of this approach weakens, and the time they remain invisible gets shorter.
Utility / Feature | Malicious Function | Why It Evades Detection |
PowerShell | Enables remote command execution on other systems. | It is a trusted Microsoft automation tool, so malicious scripts look like normal IT operations . |
WMI (Windows Management Instrumentation) | Abused to download malicious payloads from the internet or exfiltrate stolen data. | Used for reconnaissance, dumping credentials, and moving laterally across the network. |
Certutil.exe | Creates persistent access by setting up jobs that execute attacker code at specific times. | It is a legitimate certificate authority utility that is explicitly allowed by most security controls . |
Scheduled Tasks | Used to establish persistence and modify system configurations. | Malicious tasks are disguised as legitimate system maintenance jobs . |
Windows Registry | Malicious tasks are disguised as legitimate system maintenance jobs. | Allows attackers to execute commands without uploading files or using suspicious protocols. |




