Operation Endgame: Disrupting Transnational Cyber Threats
November 15, 2025
Operation Endgame marked a turning point in Europe’s collective counter-ransomware posture. It was not a routine
Iran’s Expanding Cyber Pressure Matrix: From Personal Coercion to Aerospace Intrusions
November 20, 2025
Iran’s cyber apparatus continues to evolve into an increasingly aggressive, multi-layered instrument of geopolitical pressure. What
APT42’s SpearSpecter Campaign: Inside Iran’s New Layered Cyber-Espionage Operation
November 18, 2025
The unfolding SpearSpecter campaign attributed to Iran’s APT42 marks a decisive evolution in state-sponsored cyber espionage.
Gootloader malware back for the attack, serves up ransomware
November 6, 2025
The resurgence of Gootloader malware illustrates the evolution of cyber threats where established tactics like SEO poisoning
German ISP Aurologic GmbH has Become a Central Nexus for Hosting Malicious Infrastructure
November 7, 2025
Aurologic GmbH operates as a central facilitator for malicious cyber activities through its services connecting clients known
Cybercrims plant destructive time bomb malware in industrial .NET extensions
November 7, 2025
Nine out of twelve NuGet packages were found to contain hidden destructive code meant to activate in
Attackers abuse Gemini AI to develop ‘Thinking Robot’ malware and data processing agent for spying purposes
November 5, 2025
The integration of AI technologies like Gemini in malware development represents a significant evolution in cyber threats
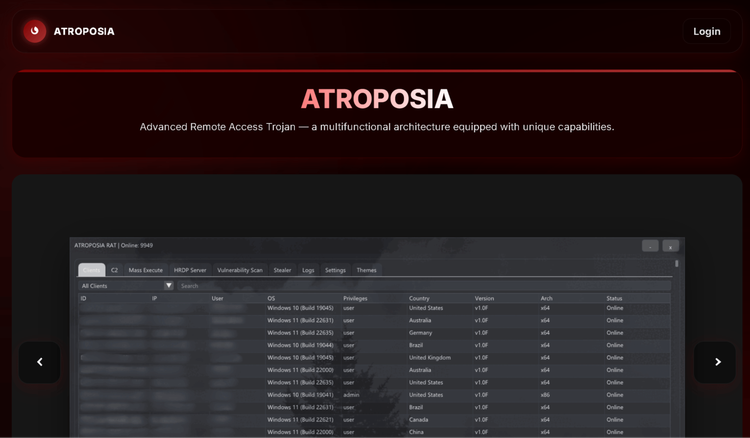
Atroposia Malware Offers Attackers Built-In Tools to Spy, Steal, and Scan Systems
November 7, 2025
Atroposia is a modular RAT that enables remote control of infected systems and data exfiltration for a
PromptLock and the New Malware Architecture: How Local LLMs Could Change Ransomware
September 3, 2025
PromptLock is a proof‑of‑concept that ties conventional ransomware tradecraft to a locally hosted large language
EggStreme: Advanced Fileless Malware Targeting Philippine Defense Networks
September 10, 2025
In early 2024, security researchers identified a highly sophisticated, previously undocumented fileless malware framework, EggStreme, used to