Securing Critical Infrastructure in the European Threat Environment
November 10, 2025
The protection of critical infrastructure has become a strategic imperative amid escalating cyber threats that increasingly intersect with geopolitical tensions and hybrid warfare. From energy grids and healthcare systems to logistics and emergency services, adversaries now target the backbone of societal stability. In response, the European Union has introduced a new cyber resilience model anchored in risk-based regulation, aiming to elevate security standards across both public and private sectors. This report explores the evolving threat landscape, the regulatory response through NIS2 and DORA, and the operational challenges facing CISOs and infrastructure operators today.
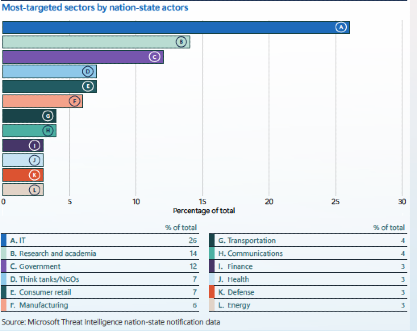
Cyberattacks have evolved into systemic threats that no longer target isolated data repositories or financial assets—they now strike at the heart of societal continuity. Critical infrastructure sectors such as healthcare, energy, logistics, and emergency services have become high-value targets for both cybercriminal syndicates and state-aligned threat actors. The 2023 Microsoft Digital Defense Report underscores this shift, revealing that modern adversaries increasingly blend digital intrusions with physical conflict, creating hybrid operations that destabilize essential services and exploit geopolitical fault lines.
These attacks are not merely opportunistic; they are strategic. They aim to disrupt emergency response coordination, paralyze energy distribution, and compromise public trust in government operations. The convergence of IT, OT, IoT, and AI systems within these sectors has created a vast, interconnected attack surface. A single vulnerability—whether in a legacy control system or a misconfigured cloud asset—can cascade across supply chains, triggering economic shockwaves and operational paralysis.
The European Regulatory Pivot: Risk-Based Resilience
In response to this evolving threat landscape, the European Union has enacted a new cyber resilience model that moves beyond compliance checklists toward dynamic, risk-based governance. Two cornerstone regulations—NIS2 and DORA—now define the cybersecurity posture expected of critical infrastructure operators.
NIS2 expands the scope of cybersecurity obligations to a broader range of sectors and entities, enforcing mandatory incident reporting, risk assessments, and technical controls. DORA, tailored to financial institutions, ensures operational continuity in the face of ICT disruptions. Together, these frameworks demand that organizations not only implement security measures but also demonstrate their effectiveness through accountability and transparency.
This shift places the Chief Information Security Officer (CISO) at the center of organizational resilience. No longer a technical advisor operating in isolation, the CISO is now a strategic leader responsible for cross-functional coordination, regulatory alignment, and cultural transformation. Their role spans board-level reporting, supply chain oversight, and the orchestration of incident response protocols that meet both operational and legal expectations.
Operational Realities: From Legacy Systems to Threat Intelligence
Despite regulatory clarity, implementation remains a formidable challenge. Many critical infrastructure operators rely on aging systems that lack modern security architecture. Patching is inconsistent, segmentation is weak, and visibility across hybrid environments is limited. Smaller entities, particularly in healthcare and regional logistics, often lack the resources to meet compliance demands without external support.
Threat intelligence integration is another persistent gap. While some sectors benefit from national-level sharing platforms, many organizations operate in silos, unaware of emerging tactics such as MFA fatigue attacks, fake CAPTCHA lures, or credential spraying campaigns. The absence of real-time detection and response capabilities leaves them vulnerable to lateral movement, privilege escalation, and data exfiltration.
To bridge these gaps, organizations must adopt a proactive posture. This includes investing in automated patching, endpoint detection and response (EDR), and AI-driven analytics that can surface anomalies before they become incidents. Supply chain security must be treated as a first-order priority, with vendors and partners held to the same standards of resilience. Incident response playbooks must be tailored to the realities of virtualized infrastructure, remote work, and cross-border coordination.
Strategic Outlook: Cybersecurity as Societal Infrastructure
The protection of critical infrastructure is no longer a technical issue—it is a matter of national security and societal stability. The EU’s regulatory model reflects this understanding, embedding cybersecurity into the operational DNA of essential services. But regulation alone is not enough. Success depends on execution: on leadership that understands the stakes, on teams that are trained and empowered, and on systems that are built to withstand not just today’s threats, but tomorrow’s unknowns.
Cybersecurity must be treated as infrastructure in its own right—resilient, redundant, and strategically governed. The fusion of intelligence, regulation, and operational discipline will define Europe’s ability to withstand the next wave of hybrid threats. And in that equation, the role of the CISO is not peripheral—it is foundational.




