Rearming the Shadows: The Next Era of Botnets and Their Geopolitical Threat
September 15, 2025
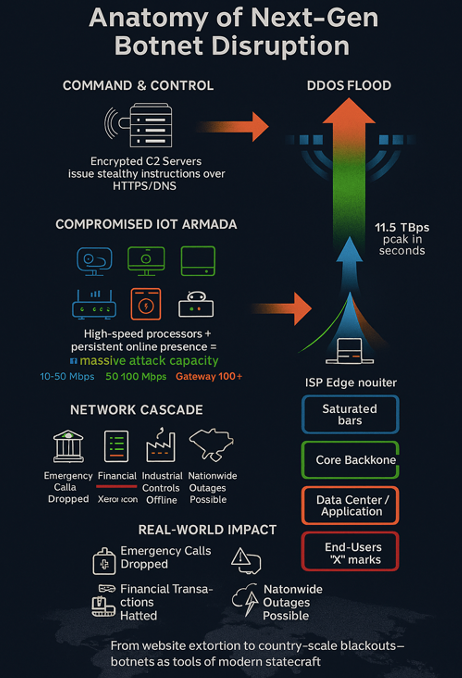
Botnets—vast networks of compromised internet-connected devices—have evolved from crude tools for knocking websites offline into strategic weapons capable of crippling entire regions. By enlisting high-bandwidth IoT gadgets like routers, cameras and smart TVs, today’s botnets can unleash traffic floods measured in terabits per second, overwhelm critical infrastructure and even sway geopolitical contests through targeted outages. This article offers a grounded look at how these next-generation botnets form, how they turn flash-bang DDoS bursts into proof-of-concepts, and why governments and network operators must urgently rethink defenses before these digital armies darken our world at will.
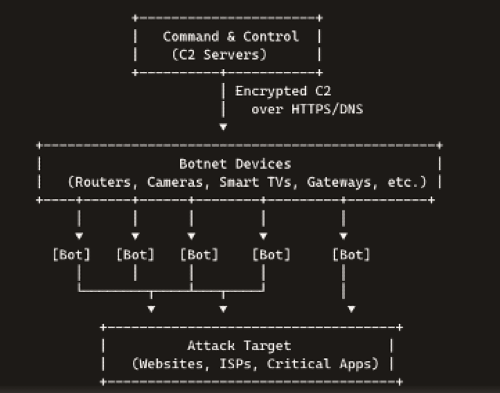
In a revealing twist, law-enforcement victories against botnets have inadvertently fueled a new generation of digital arsenals. When the FBI dismantled a massive network of compromised devices, it freed up tens of thousands of machines—only for a rival gang to seize them and forge an even more potent weapon. Today’s botnets, powered by high-speed processors in routers, cameras, and smart TVs, can no longer be dismissed as mere nuisances. They have scaled from knocking websites offline to threatening entire nations’ connectivity, ushering in a cyber arms race with profound geopolitical stakes.
Unintended Consequences of Botnet Takedowns
When the FBI disrupted one of the largest known botnets last month, roughly 95,000 infected devices were left unclaimed—and immediately snapped up by competing operators. In a frenzied scramble, the Aisuru botnet’s controllers commandeered more than one-quarter of those machines, transforming a law-enforcement success into a stepping-stone for greater chaos. As Google engineer Damian Menscher observes, the rush to re-enslave liberated devices “as fast as possible” has inadvertently supercharged the next wave of attacks.
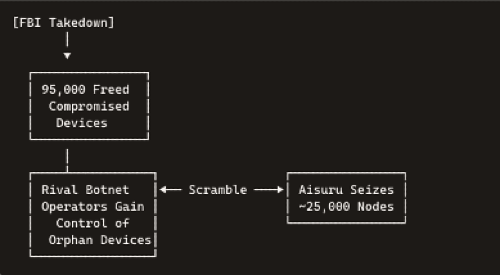
• Competing criminal groups race to claim them, supercharging rival botnets in hours.
Record-Breaking DDoS as Proof of Concept
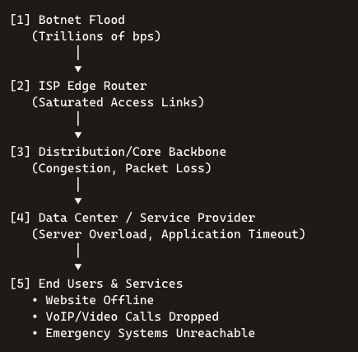
On September 1, the world witnessed the raw destructive potential of these revamped botnets. Cloudflare detected a distributed denial-of-service barrage that peaked at 11.5 trillion bits per second—enough to overwhelm over 50,000 consumer internet links simultaneously. Although the assault lasted mere seconds, it shattered previous records and served as a public demonstration of Aisuru’s raw bandwidth. Network operators report dozens of similar, short-duration spikes in recent weeks, suggesting these flash attacks are showcases rather than the botnet’s full capacity.
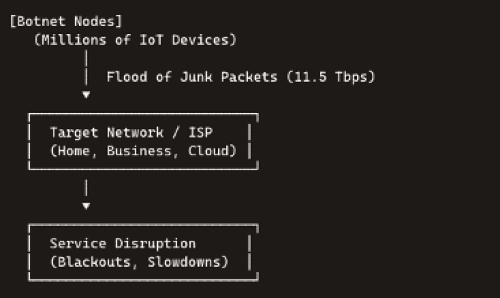
• Even brief floods cripple connectivity for thousands of users and critical services.
From Website Takedowns to National Outages
Traditional botnets focused on extorting website owners or disrupting e-commerce portals. The new breed, however, threatens broad swaths of the internet infrastructure itself. Nokia’s Craig Labovitz warns that the paradigm has shifted “from websites to countries.” With tens of thousands of devices under attacker control, adversaries could sever regional connectivity, cripple emergency communications, or blackout entire municipalities at will.
The IoT Arms Race: Leveraging Everyday Devices
Unlike earlier botnets built on compromised PCs, modern networks harness high-power IoT devices—routers, security cameras, smart TVs—with faster CPUs and greater upstream capacity. Google’s court filings reveal one such network ballooned from 74,000 Android TVs in 2023 to over 10 million devices in just two years. Originally used for ad fraud, this sprawling army could easily pivot to ransomware distribution or catastrophic DDoS campaigns.
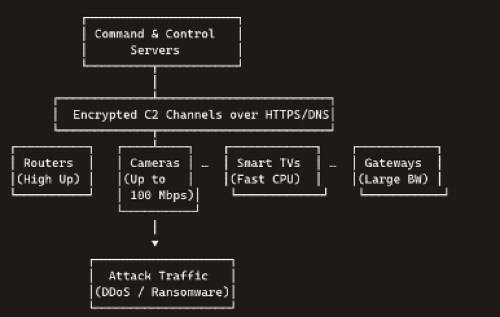
• Hardened C2 channels mask instruction flows, making detection and takedown harder.
ResHydra and the Scale-Up of Offensive Capabilities
Adding to the threat, a botnet named ResHydra has emerged with tens of millions of nodes, according to Nokia. Chris Formosa of Lumen’s Black Lotus Labs cautions that a botnet of this magnitude “would do extreme damage to a country.” Even cloud-defended services may struggle to absorb floods that large, putting critical infrastructure—power grids, financial networks, air traffic control—at unprecedented risk.
Geopolitical Implications: Botnets as Instruments of State Conflict
Denial-of-service attacks have already been weaponized by state actors. Russia’s GRU targeted Ukraine’s banking sector with DDoS assaults in 2022, softening defenses ahead of kinetic invasion. As botnets grow in scale and sophistication, they become irresistible tools for governments seeking plausible deniability. A well-timed blackout could precede military action, disrupt vote counting in elections, or coerce countries into political concessions—all without a single soldier crossing a border.
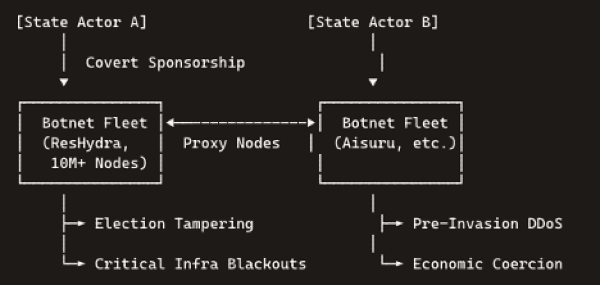
• Cyber offensives can precede or augment military operations—silencing communications, disrupting finance, or intimidating populations.
As botnets evolve from digital nuisances into instruments of statecraft, the line between cybercrime and cyberwar blurs. Without robust defenses and coordinated policy responses, tomorrow’s digital shadows may hold the power to black out cities, tip the scales of international disputes, and redefine the balance of global power.