Ransomware Expansion Across Europe: Market Dynamics, Actors, and Systemic Exposure

November 25, 2025
Ransomware activity continues to intensify across Europe, driven by a combination of expanding criminal ecosystems, increasingly professionalized gangs, and a rapid surge in attacks targeting both public and private sectors. Surveys from major cybersecurity firms underline a sustained upward curve, while insurers report mounting claims and growing uncertainty about long-term risk viability. Several incidents illustrate how deeply embedded these operations have become, from infrastructure disruption to cross-border extortion campaigns. The following synthesis brings together statistical insights, examples of attacks, industry perspectives, and insurance-market reactions, merging eight different sources into a single picture of a threat landscape that is widening in scope and impact.
Ransomware continued its acceleration through 2025, shaping itself into the most persistent global cyber threat. Across October alone, more than 700 organizations were hit, while quarterly data from multiple cybersecurity firms recorded a 36% surge in activity in Q3. Yet, even as incidents spiked, ransom payments paradoxically dropped—a sign that the market is becoming saturated, victims are increasingly resistant to paying, and newly available defensive tools are slowly shifting attacker–victim dynamics.
Analysts from Cyfirma, CrowdStrike, and several threat-intelligence teams observed a consistent rise in both reported and unreported incidents, with an expanding layer of silent victims unwilling to disclose breaches. Surveys highlighted that smaller organizations are now being hit more frequently, reflecting attackers’ preference for targets with weak security postures. Meanwhile, the ecosystem around ransomware continued to industrialize: by Q3, 85 active data-leak sites were operating, driven by the fragmentation of Ransomware-as-a-Service. LockBit’s re-emergence signaled renewed aggression in a landscape already crowded with mid-tier groups—47 of which published fewer than ten victims each, opting for stealth and slow-burn operations rather than high-profile campaigns.
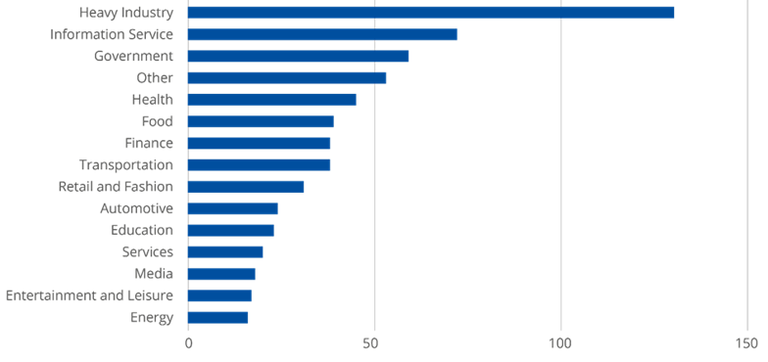
Europe remains a focal point of this global surge. CrowdStrike reported that nearly 22% of worldwide ransomware and extortion cases now involve European victims, with the UK, Germany, France, Italy, and Spain appearing consistently in leak-site disclosures. Scattered Spider typified the new wave of rapid-deployment gangs, compressing the time between access and ransomware execution to under 24 hours. European sectors most affected include manufacturing, retail, technology, and professional services—industries with complex supply chains and heavy interdependence. State-aligned groups from Russia and North Korea added another layer of complexity, merging espionage with extortion attempts, while Chinese actors increased targeting of European IP, cloud environments, and engineering-focused firms.
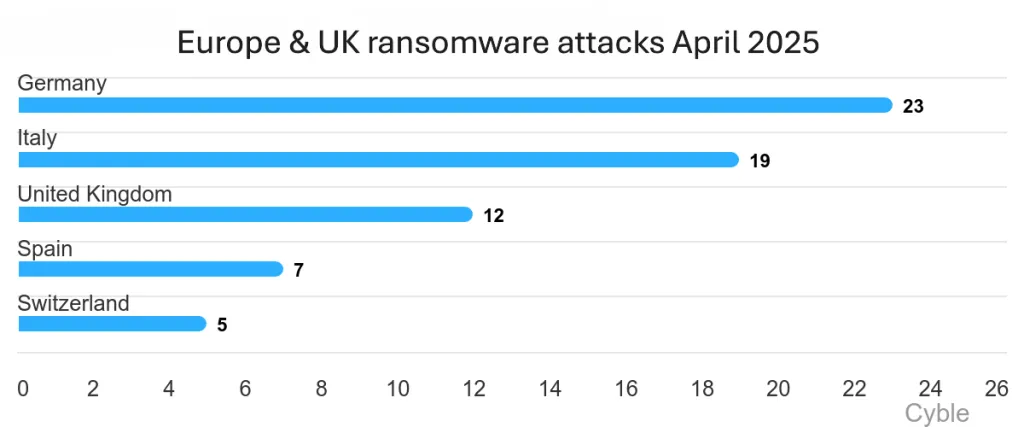
The year also exposed the fragility of interconnected supply chains. Jaguar Land Rover’s systemic breach exemplified what analysts classify as a Category 3 supply-chain ransomware event—where the point of entry lies not in the main company but deep in its network of third-party providers. Temporary production shutdowns signaled wider vulnerabilities in automotive supply chains, prompting comparisons with risks faced by Toyota, Nissan, and Ferrari. The attack reinforced calls for stricter compliance standards, industry-wide resilience frameworks, and deeper scrutiny of suppliers that now act as critical attack vectors.
Financial aftershocks were most visible in the UK insurance market. Cyber insurers paid out £197 million in 2024—more than double the previous year—with ransomware claims representing the majority. Jaguar Land Rover and Marks & Spencer were among the incidents triggering major payouts. A 230% rise in insurance claims forced insurers to reevaluate their risk models, tighten underwriting, and prepare for higher premiums as organizations struggle to match the pace and sophistication of attackers.
Despite the growth of extortion, the collapse in average ransom payments suggests that organizations are increasingly refusing to meet demands, relying more on backups, legal support, or insurance coverage. At the same time, the underground economy enabling ransomware—initial access brokers, phishing-kit vendors, exploit developers—continued to grow. CrowdStrike counted 260 active initial access brokers selling entry points into more than 1,400 European organizations, pushing the barrier to entry even lower for new or inexperienced criminal groups.
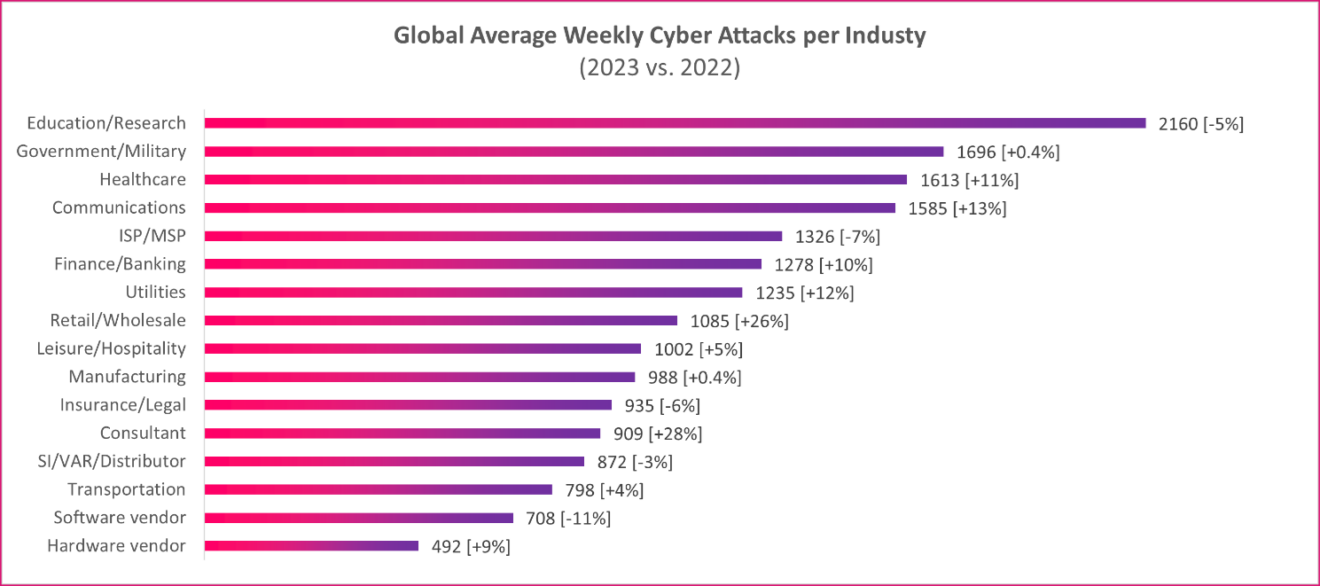
The overall picture is one of a ransomware ecosystem expanding in volume, diversity, and operational speed. Attackers are adopting more industrialized methods and aligning with geopolitical agendas, while defenders continue to face structural weaknesses—underreporting, outdated response models, supply-chain opacity, and difficulties adapting to fast-moving threats. The surge in insurance claims and the declining ransom-payment rate hint at a defensive community that is evolving, but still reactive. Meanwhile, ransomware operators show no sign of slowing, reinforcing the notion that the threat has become a permanent fixture of the modern digital economy.