Operation Endgame: Disrupting Transnational Cyber Threats

November 15, 2025
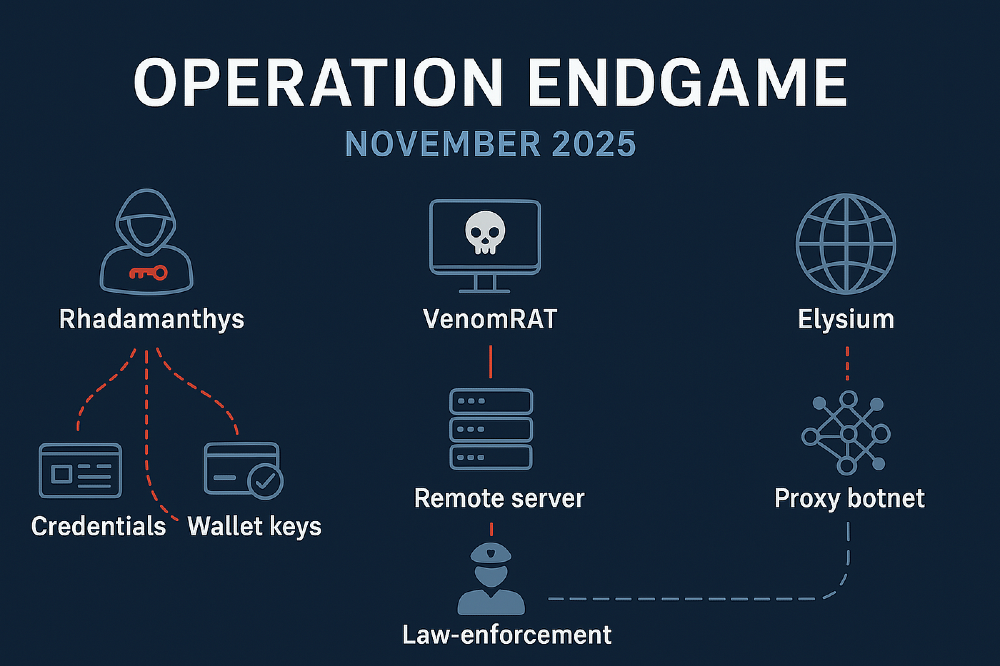
Operation Endgame marked a turning point in Europe’s collective counter-ransomware posture. It was not a routine takedown but the first fully coordinated, multi-jurisdiction disruption that directly targeted the core infrastructure underpinning global ransomware distribution. Europol and a coalition of over 30 partners dismantled 1,025 servers dispersed across Europe, North America, and Asia. These servers represented the operational backbone of various malware distribution networks, including dropper ecosystems that historically enabled some of the most damaging ransomware deployments. Early intelligence linked parts of this infrastructure to well-known loader families often used as first-stage infection vectors. The operation’s emphasis was not on small, isolated nodes but on coordinated infrastructure clusters that served thousands of daily infections.
Intelligence sources describe Endgame as the most quantitatively significant infrastructure disruption ever executed under Europol oversight. The servers identified were responsible for supporting wide-scale phishing, botnet expansion, credential harvesting, and ransomware deployment. Several neutralized nodes were involved in command-and-control traffic for loaders that have repeatedly been connected to high-impact campaigns in Europe and the United States. A number of these loaders historically fed into ransomware-as-a-service chains, which points to a deliberate Europol strategy: cutting the pipeline rather than waiting for end-stage criminal operators.
Endgame’s geographic footprint reveals a shift in cybercriminal hosting habits. More than half of the servers taken down were located in EU member states, often rented through low-cost VPS providers with weak verification. Others were detected in Eastern Europe, Turkey, and East Asia, reflecting an infrastructure mosaic typical of hybrid criminal ecosystems that mix professionalized groups with loosely affiliated actors. The operation yielded forensic images, logs, and payment traces suggesting that these nodes generated several million euros in cumulative criminal revenue. Intelligence estimates indicate that at least 15 major cybercriminal clusters were directly affected, although Europol disclosed arrests only in specific jurisdictions where attribution confidence was highest.
A qualitative assessment shows that Endgame disrupted three key dimensions of modern ransomware operations: scale, automation, and service-oriented distribution. The targeted strains were not classic ransomware payloads but the enablers: loaders, droppers, and botnet tools that transformed ransomware from targeted crime into global industrial-scale activity. Removing this layer increases operational friction for ransomware actors, forcing them to rebuild infrastructure, redistribute tasks, and reconstitute partnerships with bulletproof hosting providers.
The operation also demonstrated a deeper integration of private-sector threat intelligence. Several cybersecurity firms provided malware telemetry, botnet mapping, and cross-referenced C2 graphs. Private researchers had tracked parts of the infrastructure for months, correlating malware lineage and cluster behaviors. This marks a continuation of a broader trend where law enforcement relies more heavily on commercial CTI feeds, log pipelines, and sinkholed traffic analysis.
Quantitatively, the 1,025 servers dismantled represent nearly double the scale of previous Europol operations such as Operation SpecTor or the Emotet takedown. Analysts estimate that the infrastructure neutralized under Endgame accounted for approximately 5 to 10 percent of global malicious loader traffic during peak operational periods. While not eliminating the overall ecosystem, the blow is comparable to earlier high-profile disruptions that forced cybercriminal groups to undergo multi-month recovery cycles. Europol’s messaging suggests an intention to maintain long-term pressure, including follow-up seizures, legal warrants, and international subpoenas targeting cryptocurrency flows linked to the takedown.
Endgame’s strategic significance lies in its timing. The operation unfolded amid rising ransomware intensity across European public services and industrial operators, with insurance markets reporting record claims and enterprises suffering prolonged operational disruptions. Law enforcement agencies recognized that simply arresting individuals had limited long-term impact when the infrastructure layer remained resilient. Endgame reversed that logic, prioritizing systemic disruption over individual prosecution. It reflects a growing belief that cutting off enablers may be more destabilizing to ransomware groups than arresting operators who can be rapidly replaced.
Looking ahead, the intelligence picture suggests that the disrupted collectives will likely regroup, but with weakened operational cohesion. Rebuilding 1,025 servers demands capital, coordination, and risk-tolerant hosting partners — all more difficult under heightened international scrutiny. Some clusters may merge with larger, more sophisticated groups, creating new hybrid ecosystems. Others may pivot to fraud or data theft operations until ransomware infrastructure can be rebuilt.
Operation Endgame stands as a reminder that cybercrime is increasingly vulnerable to coordinated, intelligence-driven offensives. It shows that multinational takedowns can meaningfully disrupt ransomware supply chains when executed at sufficient scale, targeting infrastructure rather than surface-level actors. For now, the ecosystem is destabilized, the loaders are weakened, and the global ransomware machinery faces its first major systemic interruption of the decade.