“NightEagle and the Microsoft Battlefield: Zero-Day Exploitation in the Digital Great-Power Contest”

July 5, 2025
In the evolving landscape of cyber operations, Microsoft’s enterprise infrastructure has emerged as a critical theater for state-level maneuvering. Threat groups are no longer conducting isolated intrusions; they are engaging in a low-intensity, long-term conflict that mirrors geopolitical rivalries in the physical world. NightEagle, a newly identified APT, exemplifies this trend by exploiting a zero-day vulnerability in Microsoft Exchange to infiltrate Chinese military and high-tech sectors. Meanwhile, separate operations targeting Microsoft SharePoint reveal a parallel approach by China-linked actors against Western interests. Both campaigns demonstrate a shared tactical doctrine: leveraging undisclosed zero-days, stealing server-side cryptographic keys, bypassing authentication, and deploying persistent webshells while blending into legitimate administrative traffic. These attacks highlight Microsoft’s ecosystem as a trusted yet vulnerable strategic terrain where espionage, financial gain, and national security intersect, turning software infrastructure into the frontline of an ongoing digital great-power contest.
A newly identified threat group known as NightEagle (also tracked as APT-Q-95) has been quietly targeting Chinese military and high-tech organizations by exploiting a previously unknown vulnerability in Microsoft Exchange. Active since at least 2023, the group operates at night (Beijing time) and rotates its command-and-control infrastructure at high speed, which is why Chinese analysts refer to it as “fast, accurate and ruthless.” The campaign focuses on strategic sectors such as semiconductor manufacturing, quantum research, artificial intelligence and defense procurement. According to QiAnXin’s RedDrip Team, the attackers exploit a zero-day in Exchange to steal the machineKey, bypass authentication, implant a backdoor directly into the IIS component of Exchange, and remotely access any mailbox on the compromised network. The backdoor is delivered through a .NET loader and supported by a customized version of the open-source “Chisel” tunneling tool, which is configured to automatically establish an encrypted SOCKS tunnel every four hours.
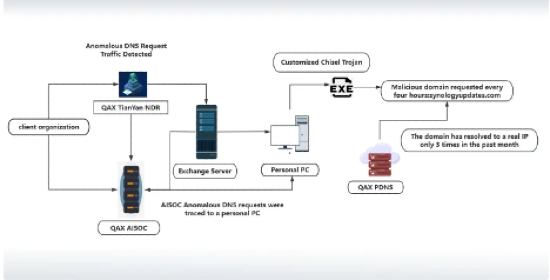
This enables long-term, covert exfiltration of sensitive data over HTTPS and allows the actor to maintain access even through server reboots and patch cycles. The group only attacks organizations that operate at the intersection of advanced technology and national security, suggesting a pure espionage motivation. Chinese analysts believe the operators may actually be based in North America, noting that all activity occurs during China’s night-time hours and that the code exhibits typical Western development conventions. The significance of the NightEagle campaign lies in the continued exploitation of Exchange as an initial access vector combined with the deliberate use of legitimate penetration tools to blend into normal network behavior. In other words, Microsoft’s core communication platform remains a high-risk target, and the offensive tradecraft has shifted from broad infection to quiet pre-positioning inside highly strategic environments. The underlying lesson is that even fully patched infrastructure is vulnerable to credential compromise and custom zero-day exploitation, and that state-level actors are now moving faster than traditional defensive cycles can adapt.
"Microsoft as a Battleground: Exploitation Across Products"
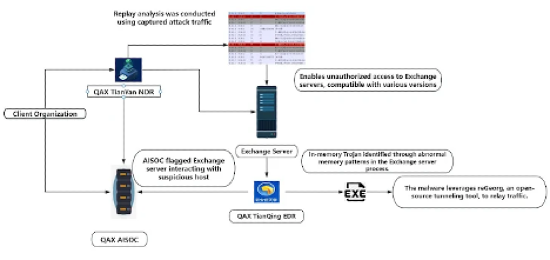
Although the NightEagle campaign specifically targets Microsoft Exchange for Western-facing financial and strategic gain, the SharePoint intrusion illustrates the same playbook being leveraged for China-linked espionage. Both operations exploit undisclosed zero-days to steal Microsoft server-side cryptographic keys, bypass authentication, and deploy persistent webshells, turning trusted collaboration infrastructure into a covert battlefield. By leveraging legitimate administrative tools such as Chisel, ASPX shells, and PowerShell, the attackers blend seamlessly into normal network traffic, making detection difficult. While NightEagle remains unattributed, the SharePoint operation is linked to the Linen Typhoon / Violet Typhoon cluster. The technical overlap demonstrates that both Western and China-linked actors are treating Microsoft’s ecosystem as a strategic theater for long-term, low-intensity cyber conflict, underscoring its role as a critical terrain in the ongoing digital great-power contest.
Download the Full Report (pdf)




