Landfall Spyware – Anatomy of a Silent Android Espionage Campaign in the Middle East

November 18, 2025
In the expanding battlefield of mobile cybersecurity, the Landfall spyware campaign stands out as one of the most technically refined and geopolitically significant operations uncovered in recent years. Identified by Palo Alto Networks’ Unit 42, Landfall represents a disturbing leap forward in the weaponization of everyday smartphone features—turning a simple image file into the gateway for a full-scale espionage operation.
This report reconstructs how Landfall silently infiltrated Samsung Galaxy devices, remained undetected for months, and ultimately exposed the vulnerabilities inherent in modern mobile ecosystems. Beyond its technical sophistication, Landfall’s activity points toward targeted surveillance in the Middle East, shedding light on the growing use of commercial-grade spyware as a geopolitical tool.
The Landfall campaign is believed to have begun in mid-2024, initially appearing as a series of unexplained crashes and sensor malfunctions on Samsung Galaxy devices. What seemed like routine glitches soon revealed a coordinated cyber-espionage effort exploiting a zero-day vulnerability in Samsung’s proprietary image-processing framework.
The flaw—later designated CVE-2025-21042—allowed malicious actors to compromise devices through manipulated image files. Critically, this was a zero-click exploit: victims did not need to open or interact with the image. Simply receiving it was enough to trigger the infection. Once the exploit executed, Landfall embedded itself deep within the device. It granted attackers expansive surveillance capabilities: access to photos, encrypted messages, call logs, contacts, stored documents, and real-time geolocation. Even more concerning, the spyware enabled remote activation of microphones and cameras, effectively converting the phone into a pocket-sized intelligence collection platform.
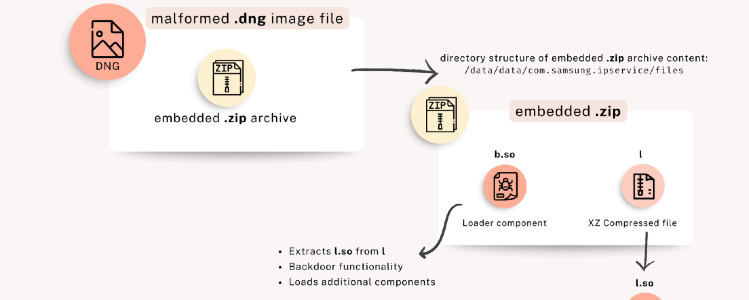
A Campaign Hidden in Everyday Traffic
Researchers discovered that Landfall made deliberate efforts to appear ordinary. Its traffic blended seamlessly into legitimate network flows, and its internal architecture featured layers of obfuscation to hinder detection. The initial signs of compromise surfaced when analysts observed subtle anomalies in network telemetry from several Samsung devices—patterns that seemed benign until cross-referenced with abnormal sensor events and device instability.
Only after extensive forensic analysis did investigators attribute these irregularities to the same malicious source: a stealth spyware implant operating continuously in the background.
Evidence suggests that Landfall was active for nine months or more, remaining operational until Samsung issued a patch in April 2025. The vulnerability affected a wide range of high-end models—including the Galaxy S22, S23, S24, Z Flip4, and Z Fold4—suggesting an operation designed to target individuals with higher-value smartphones, often associated with professional or governmental use.
A Targeted Operation with Geopolitical Weight
While the technical details alone make Landfall a significant case, its targeting profile introduces a pivotal geopolitical dimension.
Indicators point toward a focused espionage campaign in the Middle East, with victims linked to sectors traditionally surveilled by state-aligned entities:
• governmental personnel
• defense-adjacent professionals
• senior executives in strategic industries
• journalists and civil society actors in sensitive political environments
This geographic clustering, combined with the sophistication of the exploit chain, suggests operators with access to specialized resources, likely supported by or aligned with a nation-state. Though attribution remains unconfirmed, the operation aligns with broader regional patterns involving advanced commercial spyware vendors and state-sponsored intrusion sets seeking strategic intelligence advantages.
Technical Precision and Long-Term Persistence
Landfall’s architecture reflects a level of engineering designed not merely for access but for longevity and plausible deniability.
Key attributes include:
- Highly customized payloads: every post-exploitation sample uncovered by researchers had a unique hash, complicating signature-based detection.
- Stealthy communication: command-and-control servers mimicked benign traffic, reducing forensic traces.
- Zero-click infection vector: a technique typically associated with top-tier offensive cyber units.
This combination allowed the spyware to burrow deeply into device systems, maintain persistence for months, and continue exfiltrating data without raising red flags from common mobile security tools.
Response, Mitigation, and the Road Ahead
The Landfall discovery triggered an urgent response from Samsung, culminating in a security patch in April 2025. Cybersecurity teams globally have since urged users to apply updates immediately, disable automatic media downloads, and monitor devices for abnormal behavior. But the implications are broader than a single vulnerability.
Landfall illustrates the emergence of a new class of mobile threats—silent, targeted, and engineered for geopolitical espionage. It confirms that smartphones have become one of the most valuable intelligence assets in the world, and that adversaries are increasingly willing to invest in zero-day capabilities to exploit them. As global tensions and regional rivalries intensify, the Landfall operation serves as a stark warning: the line between commercial spyware and state-level cyber weapons is fading, and everyday digital interactions are now part of the modern battlefield.




