Kraken Ransomware: The Calculated Successor to HelloKitty
November 13, 2025
The emergence of Kraken ransomware marks a pivotal moment in the evolution of cyber extortion. Rising from the remnants of the HelloKitty cartel, Kraken demonstrates a shift from noisy, opportunistic attacks to disciplined, intelligence-driven operations. Unlike its predecessors, Kraken does not simply encrypt indiscriminately; it benchmarks, adapts, and calibrates its payload to the victim’s environment. This calculated approach—combined with cross-platform targeting of Windows, Linux, and VMware ESXi—signals a new era of ransomware campaigns designed for maximum efficiency and impact.
Kraken’s operational chain reveals a deliberate choreography: entry through exposed protocols such as SMB and RDP, persistence maintained via encrypted tunnels, exfiltration of sensitive data through SSHFS, and finally, the decisive act of encryption. The result is not just disruption but leverage—an extortion model that thrives on both technological precision and psychological pressure.
This introduction sets the stage for understanding Kraken not merely as malware, but as an intelligence-informed adversary reshaping the ransomware landscape.
Kraken is a new ransomware group that grew out of the old HelloKitty operation. Unlike older ransomware that just locks files right away, Kraken is smarter. It first checks how strong the victim’s computer is, then decides the best way to attack. This makes it faster, harder to stop, and more dangerous for businesses.
The rise of Kraken ransomware is not an isolated phenomenon but part of a wider geopolitical and economic landscape that has nurtured the professionalization of cybercrime. Emerging from the remnants of the HelloKitty cartel, Kraken embodies the transition from opportunistic ransomware gangs to disciplined, intelligence-informed operators. Its methods—benchmarking victim systems, cross-platform targeting, and stealthy exfiltration—reflect a calculated approach designed to maximize leverage while minimizing exposure.
This evolution cannot be understood without considering the global context. The fragmentation of international law enforcement cooperation, the safe havens provided by jurisdictions reluctant or unable to prosecute cybercriminals, and the lucrative economics of data extortion have created fertile ground for groups like Kraken. In regions where political instability or strained relations with Western powers prevail, ransomware actors find both protection and plausible deniability. The result is a shadow economy where technical sophistication meets geopolitical opportunity.
Kraken’s operational chain—entry through exposed protocols, persistence via encrypted tunnels, exfiltration of sensitive data, and final encryption—illustrates a choreography that is both technical and strategic. It is not merely about locking files; it is about shaping the victim’s decision-making under duress. The double-extortion model, now standard practice, leverages both technological disruption and reputational risk, forcing organizations to weigh financial loss against public exposure.
In early 2023, a new ransomware variant called Kraken emerged, a continuation of the well-known HelloKitty operation, which has since evolved into a sophisticated malicious endeavor targeting Windows and Linux/VMware ESXi systems. The Kraken ransomware showcases an innovative feature that benchmarks the encryption capability of compromised machines to determine whether to carry out full or partial data encryption. This capability results in faster execution of ransomware encryption while minimizing the risk of detection. The operational methodology of the Kraken ransomware begins with the exploitation of Server Message Block (SMB) vulnerabilities found in internet-facing assets, allowing attackers to gain initial access to target environments. Once inside, attackers extract administrator credentials and utilize Remote Desktop Protocol (RDP) to establish a second entry point into the system. They then employ tools such as Cloudflared and SSHFS to maintain persistent access and to facilitate lateral movement across the network, eventually targeting valuable data for extraction.
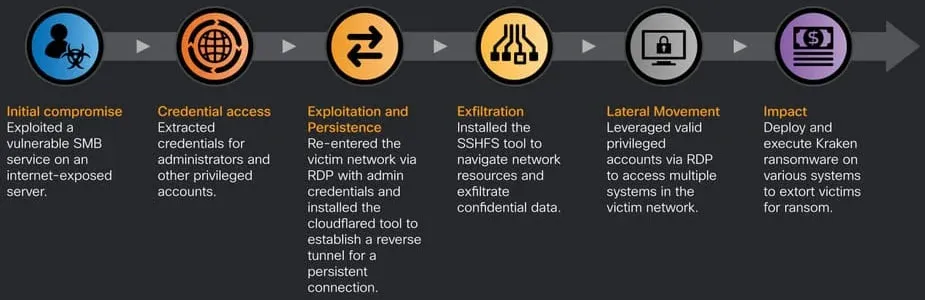
The attack chain is carefully orchestrated, employing techniques that include the immediate deletion of shadow copies and backup files before encryption begins. Researchers at Cisco note that during the preliminary phase of an attack, Kraken creates temporary files to assess machine performance under encryption load conditions. This process aids the ransomware in deciding on the optimal method for full or partial encryption based on the machine's performance metrics, emphasizing discretion and efficiency in resource use to avoid alerting security defenses.
When Kraken executes its malicious payload, a meticulously designed four-tiered encryption scheme is employed. The Windows variant systematically identifies SQL Server instances, network shares, local drives, and virtual machines operating within Hyper-V environments, encrypting data files as deemed necessary. The Linux and ESXi versions follow a similar methodology, effectively processing virtual environments to maximize impact. In a noteworthy instance, the ransom demand issued by Kraken reached $1 million, showcasing the financial pressures exerted on victims post-attack.
Additionally, the ransomware operators have initiated a cybercrime forum known as “The Last Haven Board,” intended to facilitate secure communication amongst criminals. The operational tactics not only highlight a rampant increase in ransomware threats but have also tied back to previous activities associated with HelloKitty, indicating a possible resurgence or evolution within ransomware services available on the dark web. Victims have been reported across multiple countries including the United States, the UK, Canada, Panama, Kuwait, and Denmark, contributing to the global outreach of the assault.
The emergence of this sophisticated weaponization reflects a growing trend within the ransomware landscape, and cybersecurity experts are continually updating frameworks to combat such threats. The strategies employed by Kraken present a severe reminder of the evolving tactics and sheer potential for damage orchestrated by modern ransomware operations. Cisco Talos has published various indicators of compromise that can assist organizations in identifying and responding to these attacks effectively. Furthermore, the implications of such cyber incidents extend beyond financial demands, further emphasizing the importance of proactive defenses in cybersecurity infrastructures worldwide.
-
HelloKitty cartel: A now-defunct ransomware group known for double-extortion tactics.
-
SMB (Server Message Block): A protocol for sharing files and printers over a network; often exploited for access.
-
RDP (Remote Desktop Protocol): A protocol that allows remote control of a computer; often targeted by attackers.
-
SSHFS (SSH Filesystem): A method to access and transfer files securely over SSH.
-
VMware ESXi: A virtualization platform used in enterprise servers.




