Iran’s MuddyWater Intensifies Espionage: Advanced Toolset Hits Israel and Egypt

December 2, 2025
MuddyWater, one of Iran’s most persistent intelligence-aligned threat groups, is expanding its espionage activity with a more refined and stealth-driven toolset. New incidents observed across Israel and one case in Egypt indicate a shift from the group’s historically noisy patterns toward a more precise and technically mature model. The group is now combining familiar phishing-driven intrusion methods with newly developed loaders, memory-resident backdoors, and multi-layer credential theft tools. This evolution reinforces MuddyWater’s role within Iran’s Ministry of Intelligence and Security (MOIS) and highlights the continuing escalation of regional cyber operations directed at civil, governmental, and critical infrastructure networks.
Recent investigations reveal that Iranian nation-state operators linked to MuddyWater—also tracked as Mango Sandstorm or TA450—have intensified their focus on Israeli entities, with one confirmed target in Egypt. The breadth of targeted organizations in Israel now spans academic institutions, local authorities, civil aviation, healthcare, telecommunications, engineering, manufacturing, and educational sectors. Such diversity reflects Iran’s wider intelligence priorities: surveillance, access acquisition, and strategic disruption of critical infrastructure throughout the region.
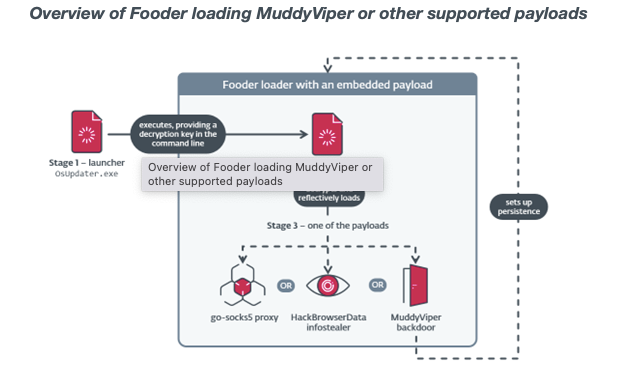
ESET’s latest analysis shows MuddyWater deploying MuddyViper, a newly developed backdoor capable of executing 20 distinct commands, exfiltrating credentials, collecting system information, running shell commands, transferring files, and retrieving browser data. MuddyViper represents a significant upgrade in the group’s technical capabilities, especially when delivered using Fooder, a custom loader disguised as the classic Snake game. Fooder loads MuddyViper directly into memory, uses custom execution delays blended with Sleep API calls, and uniquely integrates the Windows CNG cryptographic API—an uncommon approach among Iranian threat actors. These measures aim to bypass automated analysis and evade detection tools that previously identified MuddyWater’s more error-prone operations.
Initial access remains rooted in spearphishing emails that include PDFs linking to installers for remote monitoring and management tools hosted on platforms such as OneHub, Egnyte, or Mega. Unsuspecting targets download legitimate RMM software—Atera, Level, PDQ, SimpleHelp—which attackers then use as footholds to deploy their custom malware. Alongside MuddyViper, operators leverage the VAX One backdoor, which imitates Veeam, AnyDesk, Xerox, and OneDrive updater services to blend seamlessly into normal system processes.
The post-compromise environment is populated with credential harvesters such as CE-Notes (targeting Chromium browsers), LP-Notes (for staging and verifying credentials), and Blub (stealing credentials from Chrome, Edge, Firefox, and Opera). This extensive suite reinforces MuddyWater’s long-running goal of collecting wide-ranging authentication data for persistent espionage operations.
Additional intelligence from leaked Iranian cyber documents—including those attributed to APT35—reveals structured operational frameworks within Iranian state cyber units. These leaks illustrate how groups like MuddyWater are embedded within a coordinated espionage ecosystem alongside APT42, which conducts targeted intrusions against individuals and organizations perceived as threats to the Iranian regime. Such internal coordination suggests that MuddyWater may also be operating as an access broker for other Iranian units, a theory further supported by its operational overlap with Lyceum (an OilRig subgroup) during a 2025 campaign.
MuddyWater’s known history reinforces this assessment. First profiled in 2017 by Unit 42, the group has consistently relied on phishing, malicious documents, and modular malware to infiltrate networks across the Middle East. Operations such as Quicksand in 2020 targeting Israeli government and telecommunications infrastructure, a political-targeting campaign in Türkiye, and intrusions in Saudi Arabia in early 2023 all track with its evolution toward multistage, flexible espionage campaigns.
The current MuddyViper activity continues this trajectory but with clearer signs of maturation. Operators are deliberately avoiding noisy hands-on-keyboard activity, favoring memory-only execution, layered loaders, and more precise command execution. While some aspects remain detectable, the overall campaign demonstrates Iran’s investment in improving the stealth and persistence of its cyberespionage operations. Given the sectors affected—civil aviation, healthcare, local authorities, critical infrastructure—the implications extend beyond intelligence collection. They raise broader concerns about strategic pressure, regional cyber conflict, and the growing risks tied to state-sponsored intrusion capabilities in Israel and its neighboring states.