Iran’s Expanding Cyber Espionage Program: The SmudgedSerpent Campaign Against U.S. Think Tanks and Academics

November 22, 2025
Iran’s cyber espionage apparatus has entered a new phase of strategic maturity, marked by increasingly sophisticated targeting of U.S. academic institutions and policy think tanks. The SmudgedSerpent campaign, attributed to the threat actor UNK_SmudgedSerpent, exemplifies this evolution—blending social engineering, credential harvesting, and covert remote-access techniques to infiltrate environments traditionally considered low-risk. This report examines the technical tradecraft behind the operation, its geopolitical objectives, and the broader implications for research communities vulnerable to nation-state surveillance. Through detailed analysis and visual mapping of tactics, techniques, and procedures (TTPs), we reveal how Tehran’s cyber units are reshaping the intelligence landscape far beyond conventional espionage.
The latest Iranian cyber espionage activity reflects a deliberate escalation in Tehran’s efforts to infiltrate U.S. policy circles, with a renewed emphasis on exploiting academic institutions, think tanks, and individual researchers whose work influences Washington’s Iran-related decision-making. The campaign, attributed to the threat actor UNK_SmudgedSerpent, underscores a maturing Iranian intelligence ecosystem in which cyber units, security services, and foreign policy operators now work in closer alignment and with increasingly refined tradecraft. The targeting is neither opportunistic nor experimental; it is part of a coordinated intelligence collection program designed to support Tehran’s geopolitical calculations at a time of heightened Iran–Israel tensions and sustained international pressure.
The operation is rooted in familiar behavioral patterns observed in earlier Iranian-linked groups such as TA453 and TA455, but UNK_SmudgedSerpent reveals a more adaptive approach. The group combines benign pretexts with extended social engineering cycles, building rapport before initiating credential-harvesting or device-access attempts. The attackers borrow identities of real academics, analysts, and institutional figures—sometimes from organizations like the Brookings Institution—to create a credible initial engagement. They leverage widely trusted platforms such as Microsoft Teams, which reduces suspicion and allows them to bypass a portion of traditional email-based detection controls. This choice demonstrates an understanding that modern infiltration often depends less on malware and more on exploiting the user’s psychological trust in familiar communication channels.
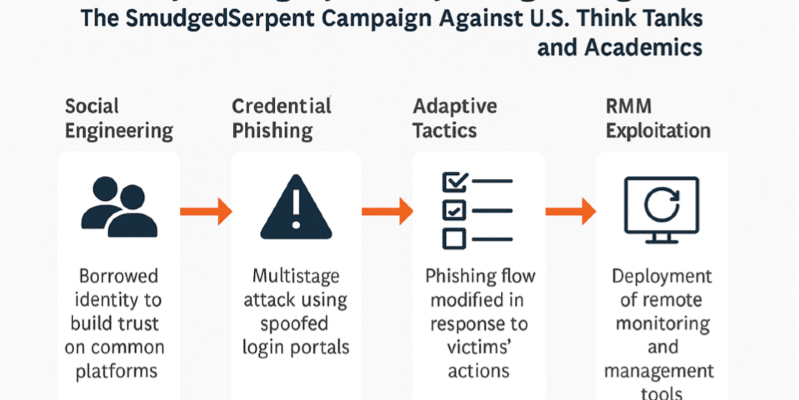
Once trust is established, SmudgedSerpent initiates a multistage intrusion sequence. The victim is steered toward a spoofed authentication portal—often a cloned Microsoft 365 or institutional login page—where credentials are harvested. Unlike earlier Iranian campaigns that relied heavily on a single phishing chain, this group adapts dynamically in response to target behavior. If a victim hesitates or appears cautious, the operators sometimes shift their method, modifying the phishing flow, changing sender identities, or adjusting lures to reduce suspicion. This reactivity points to real-time monitoring and a higher level of operator skill compared to more rigid Iranian APT playbooks of the past.
Credential capture is not the end goal. The group demonstrates capability for deeper system penetration through the deployment of Remote Monitoring and Management (RMM) software such as PDQ Connect and ISL Online. These tools, typically used for legitimate IT administration, allow continuous presence, collection of sensitive documents, monitoring of communications, and long-term surveillance. This method reduces reliance on custom malware and lowers detection rates, as RMM platforms often blend seamlessly with legitimate network traffic. The cumulative effect is persistent access rather than one-off data theft—an essential element for foreign intelligence services seeking situational awareness over months or years.
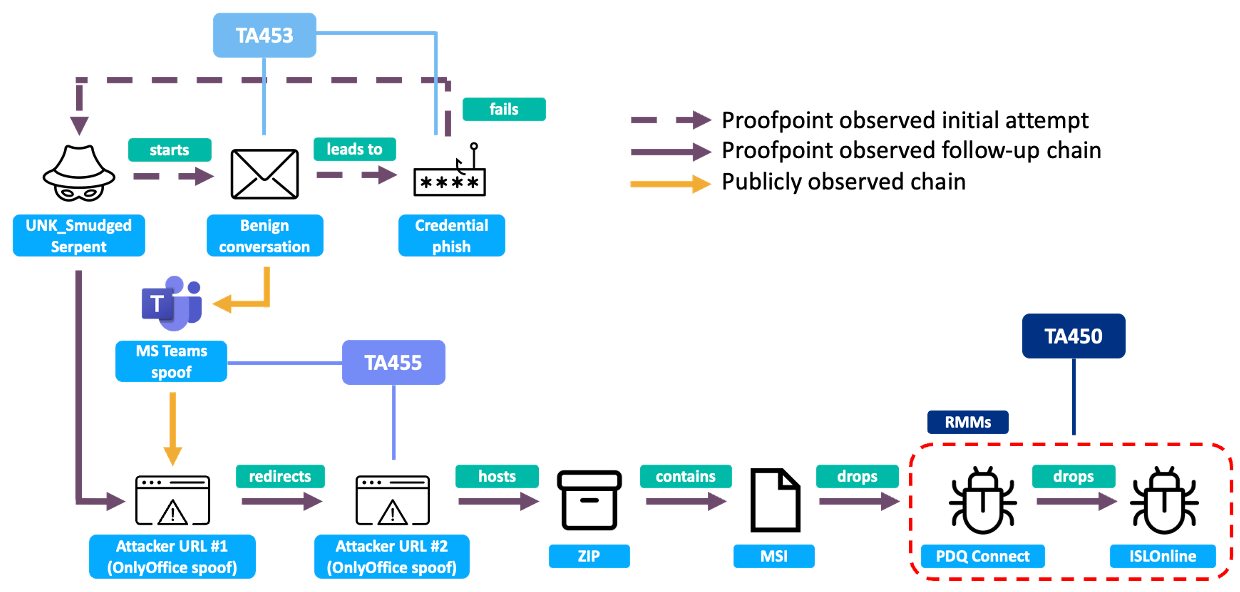
The strategic intent is clear: Iran aims to gather insight on U.S. foreign policy debates, anticipate diplomatic moves, understand internal disagreements within the policy community, and identify individuals who shape narratives about Iran. Academic environments present ideal entry points because they operate with open networks, decentralized security governance, and high volumes of external communication. Researchers often assume that their work carries low operational sensitivity, which makes them less prepared for nation-state targeting. Tehran’s intelligence apparatus understands that influencing policy is not solely about classified information but about understanding informal discussions, draft analyses, policy arguments in development, and interpersonal networks.
This operation also reflects a growing fusion between Iranian intelligence services and cyber operators. The alignment suggests institutional confidence: cyber units are trusted with tasks directly supporting Iranian geopolitical objectives, particularly as tensions rise with Israel and as Tehran seeks to counter Western pressure on its nuclear program, regional activities, and support for proxy organizations. The targeting of policy experts is not merely espionage; it is an attempt to gain leverage, anticipate diplomatic strategies, and monitor hostile narratives that may shape international coalitions against Iran.
The broader implications for the academic and research community are profound. The sector remains structurally vulnerable, often lacking zero-trust models, continuous monitoring, or advanced threat detection. Universities and think tanks seldom treat themselves as high-value intelligence targets, creating an ecosystem ripe for exploitation by advanced persistent threats. A successful compromise in these environments creates ripple effects: sensitive draft reports may be stolen or manipulated, policy arguments may be pre-emptively understood by foreign governments, and adversaries may insert themselves into discussions that help shape international relations.
SmudgedSerpent’s operations highlight the need for policy institutions to rethink their exposure. Attack vectors now extend well beyond phishing emails to include collaboration platforms, impersonation of trusted figures, and the covert use of commercial remote-access tools. As states like Iran refine their tradecraft, the line between harmless academic correspondence and state-sponsored infiltration becomes increasingly blurred. The campaign is a reminder that today’s geopolitical conflicts often begin not on battlefields but in inboxes, virtual meeting rooms, academic workshops, and research networks—spaces traditionally assumed to be benign and open.
Technical Annex: TTPs of UNK_SmudgedSerpent
- Reconnaissance & Persona Fabrication
• Tactic: Target profiling and identity spoofing
• Technique:
o Monitoring academic publications, conference rosters, and think tank outputs
o Creating fake personas using real names and affiliations (e.g., Brookings Institution)
o Establishing credibility via LinkedIn, Twitter, and institutional email lookalikes - Social Engineering via Trusted Platforms
• Tactic: Rapport-building through benign engagement
• Technique:
o Initiating contact via Microsoft Teams or Zoom
o Avoiding traditional phishing channels to bypass email filters
o Prolonged pretext conversations to lower suspicion - Credential Harvesting
• Tactic: Phishing through spoofed portals
• Technique:
o Redirecting victims to cloned Microsoft 365 or institutional login pages
o Using HTTPS and domain obfuscation to mimic legitimate sites
o Capturing credentials via real-time input monitoring - Adaptive Intrusion Flow
• Tactic: Dynamic attack modification
• Technique:
o Monitoring victim hesitation or non-response
o Switching sender identities or lure content mid-campaign
o Adjusting portal design or timing to match target behavior - Remote Access & Persistence
• Tactic: Covert system control
• Technique:
o Deploying legitimate RMM tools (PDQ Connect, ISL Online)
o Establishing long-term access without custom malware
o Blending into normal IT traffic to evade detection - Surveillance & Data Exfiltration
• Tactic: Strategic intelligence collection
• Technique:
o Monitoring communications, draft documents, and internal debates
o Capturing policy development cycles and interpersonal networks
o Exfiltrating data over encrypted channels or cloud sync




