Gootloader malware back for the attack, serves up ransomware
November 6, 2025
The resurgence of Gootloader malware illustrates the evolution of cyber threats where established tactics like SEO poisoning are combined with sophisticated obfuscation methods. The rapid progression from infection to domain controller compromise highlights the urgency for organizations to bolster their detection and response mechanisms.
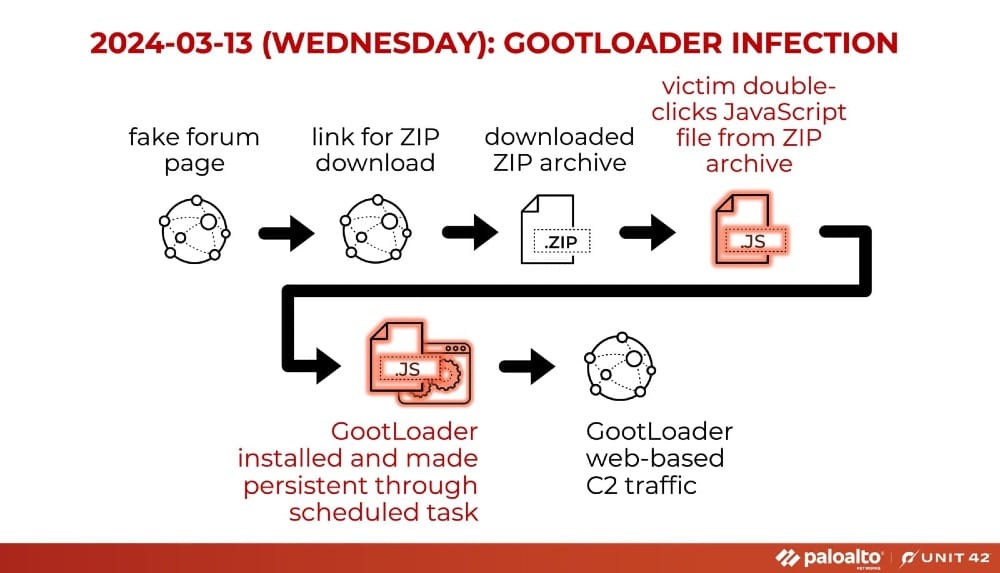
Gootloader malware attributed to the cybercriminal group Storm-0494 has become notably potent as it reenters the threat landscape. This malware typically serves dual purposes: it functions as both an infostealer and a dropper for ransomware payloads. The resurgence is marked by changes including the use of custom WOFF2 fonts for obfuscation – a clever method that renders malicious file names inscrutable to users and security tools until the malware is executed. Such obfuscation techniques significantly hinder traditional threat detection by disguising the malicious nature of payloads until they are activated by the victim.
The incident reported by Huntress highlights a streamlined attack lifecycle emphasizing the need for rapid response mechanisms. Gootloader exploits vulnerabilities in legitimate services such as using compromised WordPress comment submission features to serve malicious payloads. Once executed the malware is capable of deploying backdoors specifically the Supper SOCKS5 which allow threat actors to maintain post-exploitation persistence and conduct reconnaissance operations seamlessly. Notably the quick lateral movement achieved by the attackers leveraging tools like Impacket for remote commands underscores a concerning trend where attackers can gain domain-level access in under a day post-infection often targeting backup systems for deletion before encryption begins.
The implications of this resurgence are significant as organizations often remain unprepared for such swift incursions reinforcing the necessity for real-time monitoring and rapid incident response protocols. Moreover the coordinated partnership between Gootloader and Vanilla Tempest underscores a broader trend in the cyber threat landscape where specialized groups are not only executing attacks but are collaborating to enhance the efficacy and speed of their operations. This evolving landscape demands constant vigilance and updated defensive strategies particularly against ransomware threats that leverage such efficient methodologies.