Exploiting the Oracle Gap: Unpacking the Cl0p Breach at The Washington Post

November 16, 2025
The cyberattack against The Washington Post marks a significant escalation in the ongoing wave of large-scale data breaches driven by sophisticated ransomware groups. At the center of this incident is Cl0p, a Russian-speaking cybercriminal organization known for exploiting zero-day vulnerabilities in widely deployed enterprise systems. By leveraging a flaw inside Oracle’s cloud-based architecture, the attackers were able to access and extract sensitive information belonging to nearly 10,000 employees, contributors, and high-profile figures connected to the publication. This breach highlights the fragility of the digital infrastructure underpinning major media outlets and underscores the growing capability of criminal groups to combine opportunistic exploitation with strategic data targeting. As investigations continue, the event serves as a stark reminder of how rapidly evolving cyber adversaries are reshaping the risk landscape for institutions that operate at the heart of public information ecosystems.
The intrusion against The Washington Post unfolded as a stark reminder of how deeply vulnerable major media institutions have become in the current cyber landscape. What emerged initially as a data breach quickly revealed itself to be a calculated operation linked to the Cl0p ransomware group, a Russian-speaking cybercriminal collective that has built a reputation for exploiting the blind spots of large organizations. The attackers leveraged a zero-day weakness inside Oracle’s cloud ecosystem and its E-Business Suite, slipping past authentication layers and reaching internal repositories that housed personal information on nearly 10,000 employees, contributors, and contractors. Among those affected was former national security advisor John Bolton, a detail that highlights how sensitive this breach truly was and how attractive such data could be for actors interested in political or intelligence-related leverage.
Investigators believe that the breach evolved from a quiet infiltration rather than a noisy ransomware event. Cl0p has increasingly shifted toward attacks where encryption becomes optional; the real value lies in data extraction, pressure, coercion, and exposure. The group’s trademark approach—double extortion—was present here in its fundamental logic: take as much data as possible, understand its strategic value, and use the threat of disclosure as a weapon. Their operation appeared to be opportunistic in timing but methodical in execution, taking advantage of a flaw in Oracle’s software before the vendor or its customers had an opportunity to react.
The Washington Post, like many organizations reliant on sprawling enterprise platforms, was exposed through a dependency it did not fully control. The attackers exploited the trust that organizations place in cloud workflows, identity mechanisms, and central data management systems. Misconfigurations within Oracle's identity functions seem to have allowed privilege escalation and lateral movement, enabling the attackers to harvest employee and contributor details without triggering immediate alarms. The incident demonstrated the weakness of older, perimeter-focused security models in environments where third-party platforms operate as integral parts of internal architecture.
The scale of the compromised data suggests that the attackers had both time and a clear understanding of where valuable information was stored. Contributor lists, internal documentation, contact details, and background data were reportedly siphoned off, raising questions about the downstream implications. Media organizations have long been targets of espionage, influence operations, and politically motivated harassment, and an actor like Cl0p, even if primarily financially driven, operates in a geopolitical grey zone where criminal operations can easily intersect with strategic interests. The exposure of high-profile contributors alone opens avenues for phishing, impersonation, and broader intelligence-gathering campaigns.
While The Washington Post has initiated an internal investigation and brought in external cybersecurity experts, the event has ignited concern across the media sector. Newsrooms tend to emphasize operational continuity and speed over security hardening, and many continue to rely on outdated or under-maintained enterprise tools. The breach underscores the discrepancy between the critical societal role of major news outlets and the relatively fragile digital infrastructure that supports them. It is increasingly clear that press institutions are becoming high-value targets not only for criminals but also for actors interested in shaping narratives or gaining visibility into the individuals behind influential reporting.
Cl0p’s continued evolution is at the center of the broader threat landscape. Their use of zero-day vulnerabilities, their rapid exploitation cycle, and their ability to compromise dozens of organizations through a single flaw reflect a level of operational maturity that challenges traditional defensive strategies. Their targeting of enterprise platforms—first file-transfer systems, now cloud-integrated business suites—reveals a deliberate move toward supply-chain-style intrusions where the compromise of one widely deployed system offers a gateway to hundreds of potential victims.
For The Washington Post, the immediate concern revolves around the integrity of personal data and the potential for reputational harm. For the rest of the industry, the incident serves as an urgent warning about the evolving nature of ransomware groups. They no longer fit neatly into financial crime categories; instead, they operate at a hybrid intersection of cybercrime, strategic disruption, and mass-scale data exploitation. The breach is not just a singular event but part of a larger pattern that will continue to pressure institutions that hold sensitive information yet operate under public-facing, high-visibility conditions.
The picture that emerges is one of a threat ecosystem growing ever more aggressive and opportunistic, exploiting the cracks in interconnected digital infrastructures. The Washington Post attack embodies this shift, illustrating how a single zero-day vulnerability in a widely trusted software suite can cascade into a compromise with national-level implications. And as the investigation continues, it is becoming increasingly evident that the breach is not just about lost data, but about the growing fragility of the digital environments supporting institutions central to public discourse.
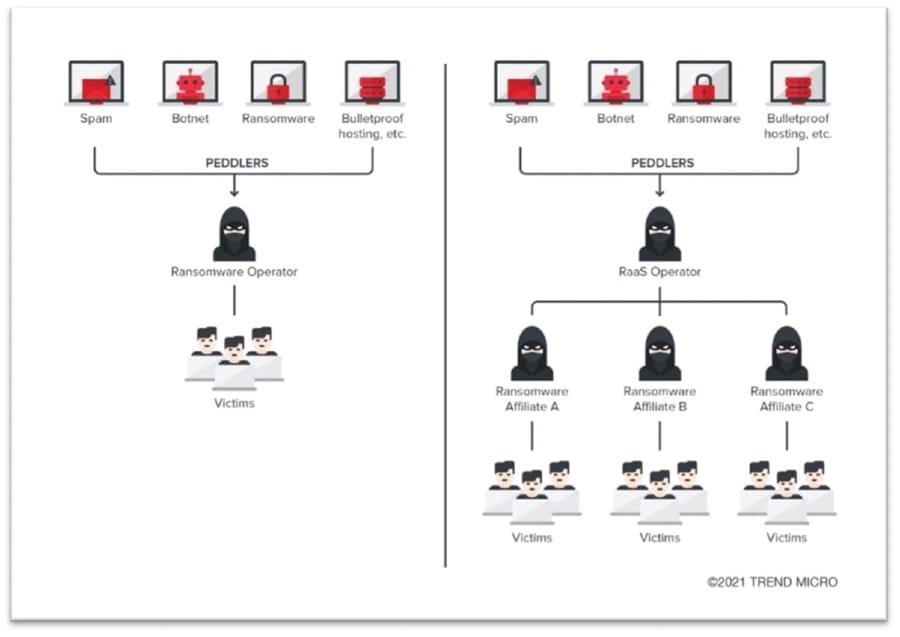
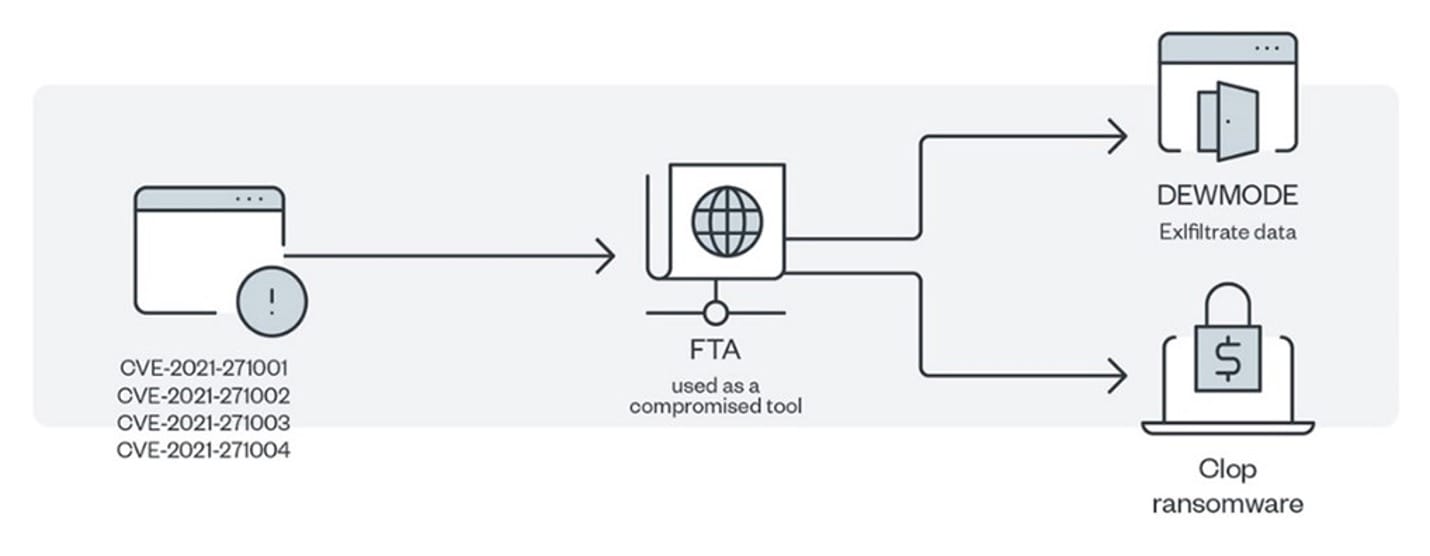
Clop is an example of ransomware as a service (RaaS) that is operated by a Russian-speaking group. It was discovered in 2019 after being used by TA505 in a spear phishing campaign.
Clop (or Cl0p) is one of the most prolific ransomware families in recent years. It’s infamous for compromising high-profile organizations in various industries worldwide using multilevel extortion techniques that resulted in huge payouts estimated at US$500 million as of November 2021. Organized efforts to dismantle ransomware cartels of a global coalition across five continents led to the arrests in Ukraine of six suspected Clop members in June 2021. Reports indicate that only parts of the ransomware’s operations were seized and taken down, such as the server infrastructure used by affiliates to disseminate the malware, and the channels used to launder cryptocurrency ransom payments.
Technical Details:
An established network of initial access brokers provides entry into victims networks. Entry is usually obtained via spear-phishing emails or compromised RDP software, either by brute-forcing passwords or exploiting vulnerabilities. At this point additional malware is installed to perform C2 and reconnaissance.
If the affected machine is not found to be a part of corporate AD environment the malware deletes itself.
Similarly, if the current keyboard layout is Georgian, Russian or Azerbaijan and the current charset used in the system is RUSSIANCHARSET then the malware will terminate.
Otherwise, it’ll try to hack the AD server using SMB vulnerabilities and Cobalt Strike. If this is successful then it’ll use the AD server admin account to propagate to other internal network machines.