EggStreme: Advanced Fileless Malware Targeting Philippine Defense Networks

September 10, 2025
In early 2024, security researchers identified a highly sophisticated, previously undocumented fileless malware framework, EggStreme, used to compromise a Philippines-based military contractor. Designed for long-term espionage, EggStreme employs reflective in-memory loaders, DLL sideloading, and session-aware keylogging to maintain persistence while evading traditional detection mechanisms. The framework’s modular structure, resilient command-and-control infrastructure, and use of lateral movement utilities such as the Stowaway proxy highlight advanced tradecraft consistent with state-aligned cyber operations in the South China Sea region. This synthesis consolidates observed technical behaviors, operational patterns, and recommended defensive measures to support threat awareness, detection, and mitigation.
Bitdefender researchers have identified a previously undocumented, multi-component fileless malware framework — dubbed EggStreme — used in a targeted intrusion against a Philippines-based military contractor. The framework is notable for its tightly integrated stages, in-memory execution model and repeated abuse of DLL sideloading to achieve persistence and covert execution. Initial access has not been determined; investigators detected the activity in early 2024 but were unable to link it conclusively to any known APT despite targeting and objectives aligning with Chinese state-sponsored espionage interests in the South China Sea region.
The operation is built around a sequence of named components. The initial deployable observed is EggStremeFuel (delivered as mscorsvc.dll), which performs host profiling, opens a command-and-control channel, spawns cmd.exe and communicates with the operator to read and write files and to dump in-memory configuration. EggStremeFuel is responsible for contacting C2 and for orchestrating the next stage, EggStremeLoader, which establishes persistence mechanisms and configures the environment for DLL sideloading. That loader in turn invokes a reflective loader (EggStremeReflectiveLoader) that loads the core backdoor — EggStremeAgent — directly into process memory, avoiding disk-resident payloads and complicating forensic recovery.
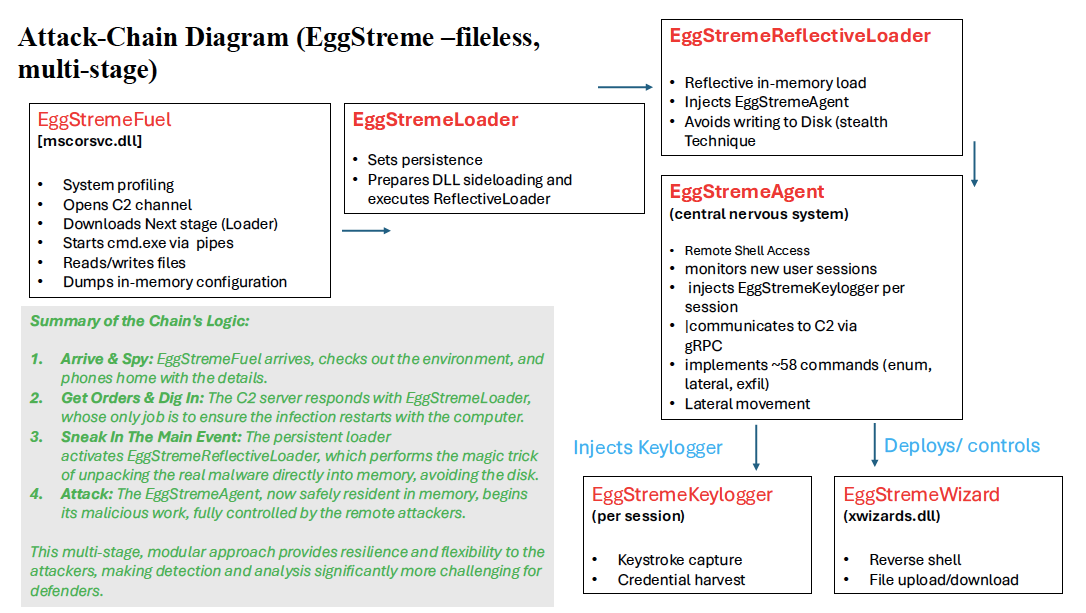
EggStremeAgent functions as the “central nervous system” of the framework. It monitors new interactive sessions and injects a per-session keylogger component (EggStremeKeylogger) to capture keystrokes and other sensitive information. The agent implements an extensive command set (reported at 58 commands), enabling reconnaissance, remote command execution, privilege escalation attempts, lateral movement, and exfiltration. Communications with C2 servers are performed over gRPC, and the actors have engineered resilience into their infrastructure by configuring multiple fallback C2 endpoints. A secondary implant, EggStremeWizard (xwizards.dll), is used as an auxiliary backdoor providing reverse shell access and file transfer capabilities; operators launch a legitimate binary that sideloads this malicious DLL, a technique repeatedly leveraged across the campaign.
Operational tradecraft includes the use of the Stowaway proxy utility to establish internal forwarding and to facilitate lateral pivoting across the victim network — a capability that, combined with the fileless reflective loaders and DLL sideloading, yields a low-disk-footprint intrusion that is difficult to detect using conventional file-based controls. Notably, one observable network behavior is the malware fetching the host’s external IP via myexternalip[.]com/raw, a small but useful artifact for detection and hunting. The campaign’s reliance on in-memory code execution, process injection, and legitimate binary sideloading demonstrates an advanced understanding of modern defensive controls and reflects intent for long-term espionage and data theft.
Attribution remains circumstantial: Bitdefender’s analysts could not tie EggStreme to a previously profiled Chinese group by code reuse or known infrastructure, yet the selection of a Philippine military contractor and the operation’s objectives are consistent with state-aligned intelligence priorities. The attackers exercised deliberate design choices favoring stealth and resilience rather than noisy, rapid destructive tactics; multiple C2 endpoints and layered loaders indicate planning for redundancy and survivability.
In sum, EggStreme represents an advanced, stealth-first espionage framework that combines fileless reflective loading, DLL sideloading, session-aware keylogging and resilient C2 to persist and move laterally within a target environment. Detection and response will hinge on behavioral and memory-oriented telemetry, network egress controls, and controls that prevent untrusted DLLs from being loaded by legitimate executables.
Download the Full Report (pdf)




