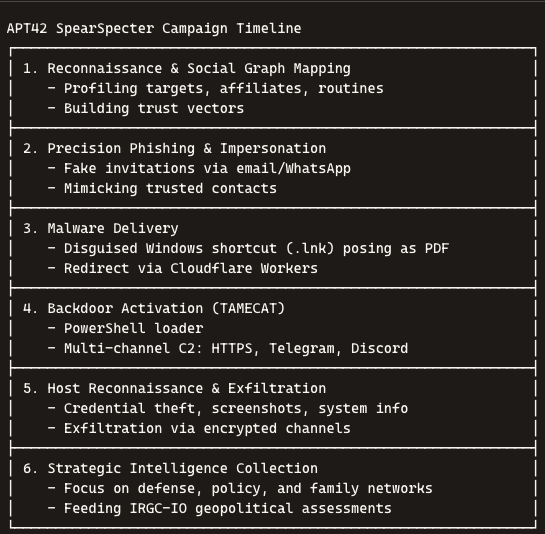
APT42’s SpearSpecter Campaign: Inside Iran’s New Layered Cyber-Espionage Operation

November 18, 2025
The unfolding SpearSpecter campaign attributed to Iran’s APT42 marks a decisive evolution in state-sponsored cyber espionage. This operation blends human-centric reconnaissance, psychological manipulation, stealthy malware deployment, and multi-platform command-and-control methods. Its targeting of senior officials, defense actors, researchers, and even family networks reveals a widening offensive posture closely aligned with Tehran’s geopolitical objectives. What emerges is a portrait of a threat group that has mastered the intersection of intelligence tradecraft and technical intrusion, shaping a new model for modern cyber espionage.
APT42’s Strategic Positioning and the Shift Toward Social-Graph Espionage
APT42, long associated with the IRGC Intelligence Organization, has moved beyond traditional targeting to embrace a broader social-graph strategy. The group now maps professional relationships, personal connections, habitual communication patterns, and sector affiliations to identify pressure points. This reflects a shift from simple credential theft to deeper intelligence harvesting designed to penetrate the professional ecosystem surrounding key individuals. By the time APT42 initiates contact, the adversary has reconstructed the target’s environment with such precision that fraudulent communications blend seamlessly into legitimate correspondence. This evolution underscores Iran’s intent to acquire strategic insights through indirect penetrations and secondary victims, widening the aperture of espionage beyond classical high-value targets.
The SpearSpecter Campaign and Its Human-Centric Initial Intrusion Methodology
SpearSpecter begins not with malware but with social psychology. APT42 leverages detailed intelligence collection to craft highly personalized phishing messages that replicate the tone, cadence, and formatting of internal communications familiar to the victim. The attackers frequently impersonate technology executives, academic collaborators, political advisors, or trusted institutional partners. The communications are convincing enough to evade even trained eyes, bypassing traditional security filters that focus on technical anomalies rather than behavioral authenticity. This intelligence-driven manipulation blurs the boundaries between cyber operations and HUMINT, forming a hybrid intrusion model that exploits cognitive trust rather than technical vulnerabilities.
From Phishing to Backdoor: The Covert Infection Chain Behind TAMECAT
The transition from social engineering to system compromise begins with a redirect chain leading to a counterfeit meeting page or document repository. Instead of delivering a harmless PDF, the attackers drop a disguised Windows LNK file whose icon and metadata mimic legitimate documents. When executed, this shortcut silently contacts a Cloudflare Workers subdomain — a tactical decision that allows malicious traffic to blend into global CDN flows. The retrieved batch script deploys TAMECAT, a tailored PowerShell backdoor that embodies the operational discipline of APT42. Obfuscated code, minimal host footprint, and execution through living-off-the-land binaries ensure that early-stage compromise remains invisible to most defensive tooling.
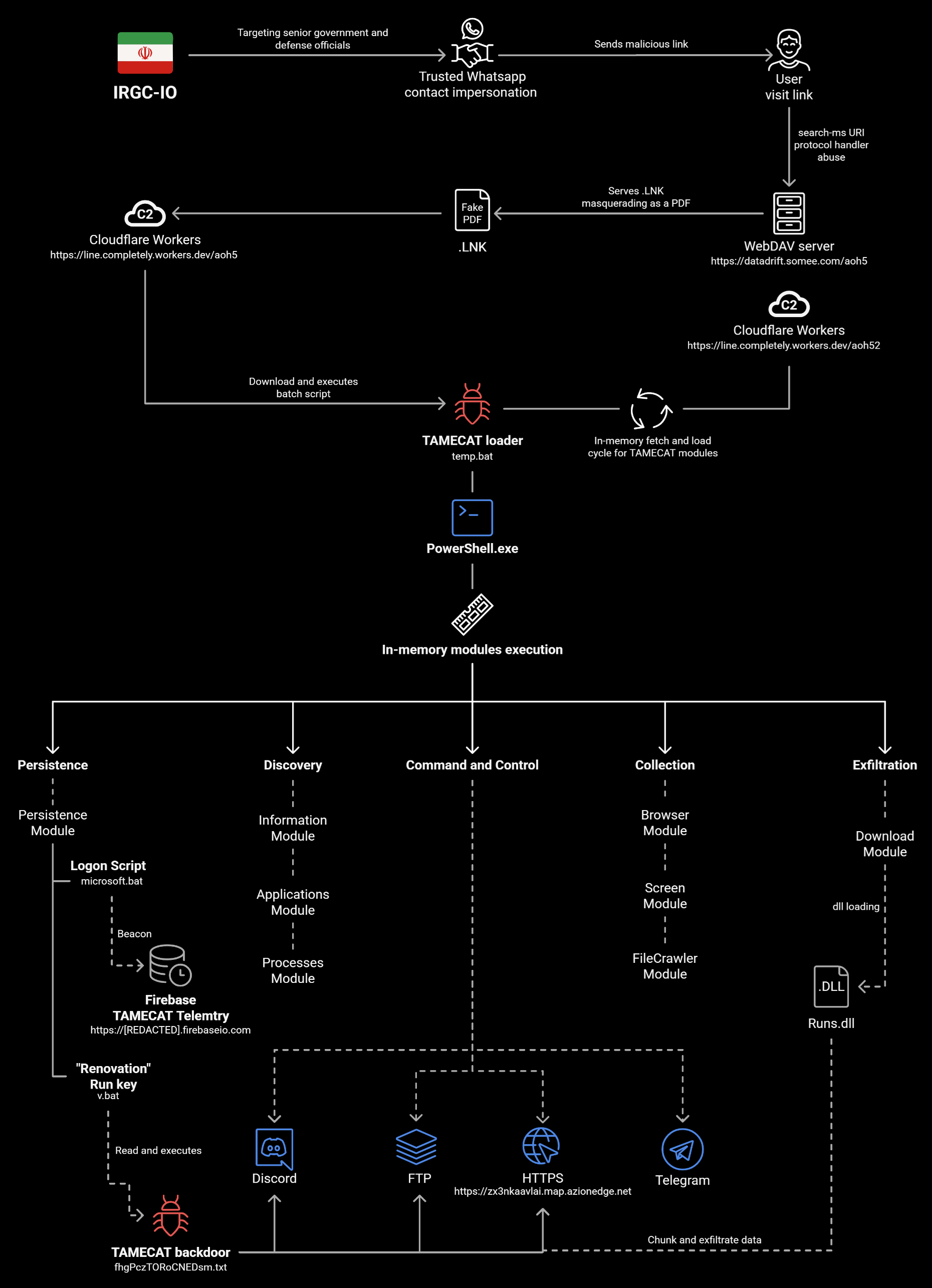
TAMECAT’s Multi-Channel Command-and-Control and Stealth Architecture
TAMECAT’s architecture reveals a sophisticated approach to long-term persistence and operational resilience. It maintains simultaneous command-and-control pathways through HTTPS, Telegram, and Discord, allowing operators to rotate communication channels dynamically or fall back to alternative platforms if one vector is disrupted. Telegram bots provide scripted orchestration, while Discord channels act as collaborative workspaces for managing multiple compromised endpoints. This fusion of public collaboration tools with covert operations embodies a deliberate strategy: if defenders cannot distinguish malicious traffic from routine employee usage, the attackers retain operational freedom. Encrypted telemetry, layered obfuscation, and selective tasking enable the malware to harvest browser credentials, email data, session cookies, and system metadata without triggering typical detection heuristics.
Reconnaissance, Exfiltration, and Deep Access into Sensitive Communication Flows
Once established, the malware initiates a systematic reconnaissance sweep. It quietly archives Outlook mailboxes, harvests browser autofill secrets, enumerates system configurations, and captures screenshots for rapid environmental understanding. Exfiltration is conducted over HTTPS or FTP, ensuring the data blends into regular traffic patterns. The campaign’s emphasis on communication surveillance shows a clear intelligence priority: monitoring decision-making processes, mapping diplomatic interactions, and capturing privileged insight into national-security discussions. APT42’s methodology reflects an understanding that the most valuable intelligence lies not only in documents but in the evolving conversations and relationships that shape policy.
Geopolitical Intent and the Integration of Cyber Operations Into Iran’s Wider Intelligence Strategy
The broader timing of SpearSpecter aligns with critical regional developments, heightening speculation regarding its strategic objectives. APT42’s focus on officials, defense networks, and trusted contacts highlights Iran’s intent to support IRGC-IO intelligence requirements with fresh, actionable data. In an era of diplomatic confrontation, sanctions pressure, and regional volatility, the Iranian regime is leveraging cyber espionage as an extension of its foreign-policy apparatus. Cyber operations now serve as an asymmetric mechanism for collecting intelligence, influencing negotiations, and compensating for geopolitical isolation. SpearSpecter demonstrates how Tehran integrates covert cyber capabilities into its national security doctrine with increasing sophistication.
Implications for Organizational Security and the Limits of Traditional Defenses
The campaign exposes persistent weaknesses in organizational security, especially in environments where human behavior presents the primary attack surface. Technical controls—email filtering, MFA, endpoint monitoring—offer limited protection against adversaries who weaponize interpersonal trust. APT42’s exploitation of legitimate communication platforms as C2 infrastructure further illustrates the diminishing utility of signature-based detection. The SpearSpecter operation is a stark reminder that the frontline of modern espionage lies in the psychological and social vulnerabilities within secure systems. As state-sponsored threat groups refine these hybrid tradecraft models, defensive strategies must evolve to incorporate behavioral analysis, contextual verification, and advanced monitoring of communication patterns.