Akira’s Playbook: How Cybercrime Became a Macroeconomic Risk
November 18, 2025
In the evolving landscape of cyber threats, ransomware has transcended its criminal origins to become a strategic disruptor of economic and national stability. Among the most formidable actors in this domain is Akira—a decentralized, financially aggressive ransomware operation that has rapidly matured into a global menace. Since its emergence in 2023, Akira has demonstrated a unique blend of technical sophistication, psychological manipulation, and geopolitical opportunism, targeting critical infrastructure and exploiting systemic vulnerabilities across North America and Europe.
This report examines Akira not merely as a malware strain, but as a case study in the professionalization of cybercrime. It explores how Akira’s tactics—from social engineering and virtualization-layer compromise to dual-extortion pressure—reflect a broader shift in the ransomware ecosystem. It also situates Akira within the geopolitical context of fragmented enforcement, asymmetric risk exposure, and transnational payment rails, revealing how attackers leverage jurisdictional gaps and regulatory pressure to maximize impact.
As ransomware continues to evolve into a systemic threat, Akira stands as a signal of the shifting balance between defenders and adversaries—a challenge that demands not only technical resilience but strategic coordination across sectors, borders, and institutions.
Geopolitical context and strategic framing
Akira ransomware sits at the intersection of cybercrime, economic coercion, and geopolitical risk. Since early 2023 it has amassed over $244 million in ransom payments, with blockchain traces touching wallets linked to the dissolved Conti syndicate, suggesting continuity of tradecraft without proving state direction. Its targeting skews toward North America and Europe, where high-value data, cyber insurance penetration, and regulatory pressure on disclosure create lucrative conditions. Law enforcement advisories from the FBI, CISA, Europol, and national agencies reflect a shift: ransomware is no longer treated as isolated criminality but as a systemic threat to economic stability and national security. Jurisdictional fragmentation, safe-harbor geographies, and cross-border infrastructure complicate takedowns and extraditions, while cryptocurrency flows enable transnational payment rails that outpace traditional financial controls.
Emergence and financial footprint
Akira’s rise mirrors the professionalization of ransomware. It operates as a dispersed network of affiliates, prioritizing agility over centralized command. The ecosystem’s financial success is driven by double extortion, disciplined leak-site branding, and negotiation portals that standardize victim engagement. Even absent proven state ties, the group’s continuity with Conti-era techniques underscores an experienced operator base and a market-oriented model that thrives where cyber hygiene, incident response maturity, and regulatory pressure are uneven.
Intrusion strategies and initial access
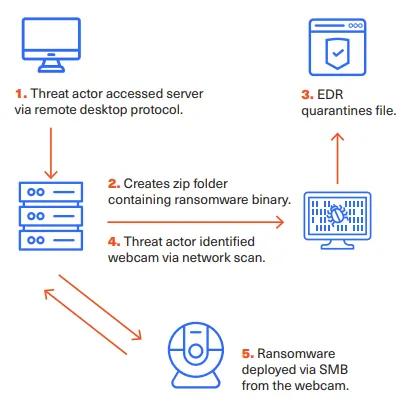
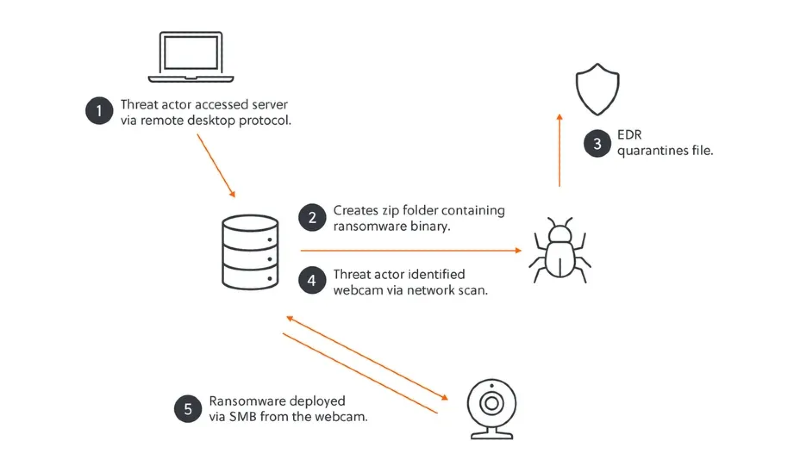
Initial access blends social engineering and exploitation: fake CAPTCHA portals and targeted phishing lures; brute-force and password spraying against VPNs (including tooling like SharpDomainSpray); and opportunistic use of exposed credentials. Timelines vary widely—intruders may persist over 40 days to map environments or pivot to rapid exfiltration and encryption within two hours when conditions allow. This operational elasticity undermines static defenses and demands detection tuned for both slow-burn intrusions and high-velocity strikes.
Post-compromise movement and stealth
Once inside, operators move laterally, escalate privileges, and deploy remote access tools (AnyDesk, LogMeIn) that blend into administrative norms. They frequently uninstall endpoint detection to degrade visibility and exploit vulnerabilities such as CVE‑2024‑40766 to maintain persistence. The blend of stealthy occupation and fast execution maximizes leverage before a coordinated response can take shape.
Sectoral targeting and victimology
Victims span manufacturing, healthcare, education, IT, and critical supply chains. High-profile cases include Stanford University, the Toronto Zoo, and BK Technologies, whose communications products support defense contractors and emergency services. Hospitals and K‑12 districts face severe consequences, driving sector-specific advisories. The targeting pattern aligns with markets where operational disruption and regulatory exposure increase payment pressure—illustrating geopolitical asymmetries: attackers exploit highly digitized, compliance-heavy economies while operating from jurisdictions with limited enforcement reciprocity.
Psychological and operational pressure tactics
Akira’s dual-extortion model pairs encryption with threats to leak sensitive internal material, compounding operational paralysis with reputational and regulatory risks. Social engineering innovations—fake CAPTCHAs and MFA fatigue (push-spam)—weaponize human factors, turning protective controls into attack vectors. The psychological calculus is geopolitical too: in regions with stringent data protection regimes (e.g., GDPR in the EU), disclosure risk elevates leverage; in the U.S., SEC cyber incident rules and sector regulators (HHS for healthcare) heighten the stakes.
Impact on virtualized and cloud infrastructures
A pivot to virtualized targets (e.g., Nutanix AHV VM disk files) widens impact by compromising hypervisor layers and shared storage. This exposes architectural single points of failure created by consolidation and multi-tenant design, challenging backup assumptions and recovery playbooks. Cloud and virtualization supply chains cross national boundaries, complicating jurisdiction and incident coordination—another geopolitical layer that slows unified response.
Economic consequences and cascading effects
Beyond ransom payments, downtime, recovery, and reputational harm impose multi-week disruptions. Insurance markets absorb spikes in claims, recalibrating premiums, exclusions, and sublimits for ransomware and business interruption. These costs ripple across suppliers and public services, turning enterprise breaches into localized economic shocks. In highly interconnected economies, serial attacks degrade confidence and growth—a reality that has moved ransomware from IT risk into board-level financial governance and macroeconomic concern.
Government response and defensive posture
On November 13, 2025, CISA and the FBI updated guidance emphasizing hardened MFA (resistant to push-spam), timely patching (including virtual platforms), resilient and isolated backups, and user training against deceptive UX artifacts like fake CAPTCHAs. Europol and national CSIRTs echoed warnings, framing ransomware as a systemic threat. Policy debates intensify: OFAC sanctions risk for paying sanctioned actors; proposals for payment bans; mandatory reporting regimes (SEC in the U.S., NIS2 and DORA in the EU) to speed collective detection and reduce information asymmetry. Yet cross-border enforcement remains uneven, and crypto tracing outpaces legal instruments, sustaining attacker viability.
Organizational preparedness and incident response
Preparedness now requires playbooks keyed to Akira’s tactics: hypervisor compromise procedures; rapid containment of MFA-fatigue incidents; segmentation and least-privilege reinforcement; anomaly monitoring in virtual management planes; and validated, offline backups with staged restore tests for VM images and shared storage. Fast channels to law enforcement (FBI/CISA, Europol, national agencies) and sector peers accelerate triage and attribution. Engagement with entities like DC3 supports technical analysis when encryption renders decryption impractical without keys.
Strategic outlook and future implications
Akira exemplifies how agile ransomware thrives in remote work patterns, fragmented defenses, and complex, transnational supply chains. The strategic balance will hinge on architecture changes that neutralize virtualization single points of failure, authentication practices resilient to human-factor exploitation, and regulatory frameworks that align incentives without driving payments underground. Public–private collaboration, real-time intelligence sharing, and harmonized cross-border enforcement are geopolitical necessities—without them, attackers will continue arbitraging jurisdictional gaps, insurance dynamics, and disclosure regimes. Akira is not merely criminal enterprise; it is a signal of a shifting equilibrium where cyber operations produce economic and strategic effects across borders, testing the capacity of liberal economies to defend digital infrastructure while preserving openness and trust.